Introduction
Here you can find all the infographics I have done, in any area of Infosec. I will update this section regularly.
You can use them for your tweets, for your classes, for whatever you want (except for the bad things).
I hope it will be useful! Feel free to come regularly, I will add new infographics based publications.
Follow me on Twitter to be informed of my new articles/infographics →  (@SecurityGuill)
(@SecurityGuill)
For your comfort, I decided to disable ads on my website.
If you like my work, feel free to support me with
Buy me a coffee
I will use this money to continue my work and my studies, but also to attend Information Security events & buy books.
Technologies
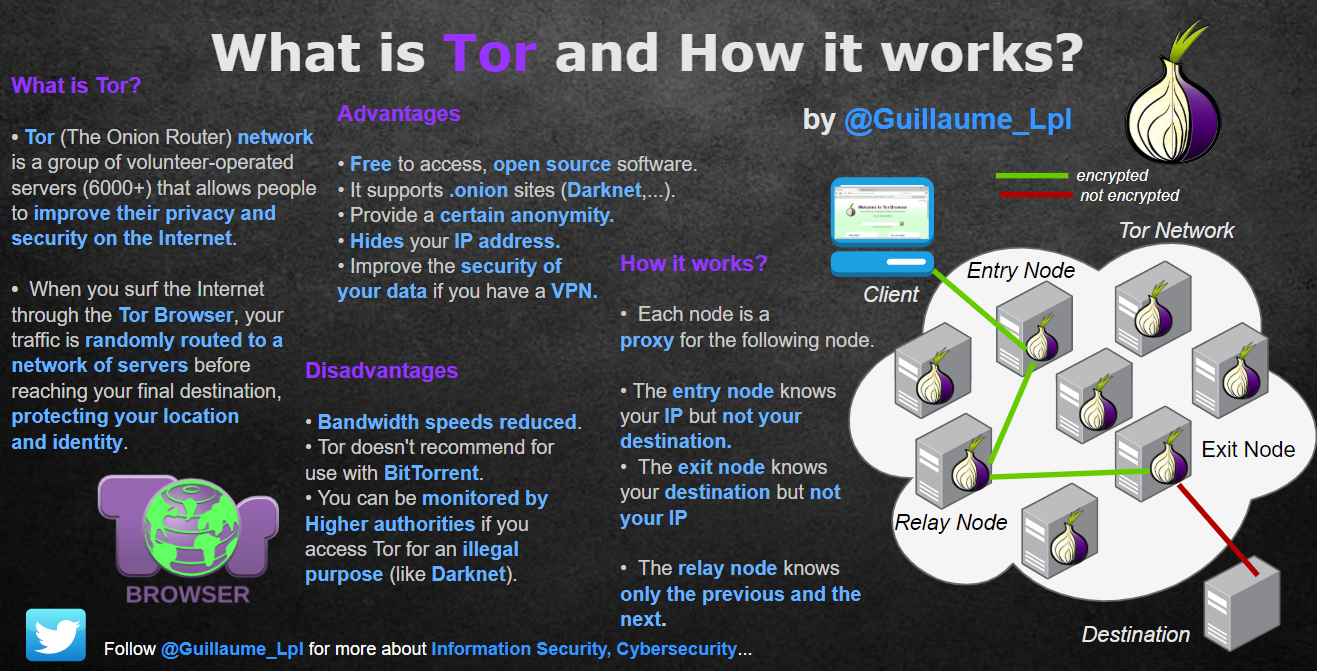
- What is Tor & How it works?
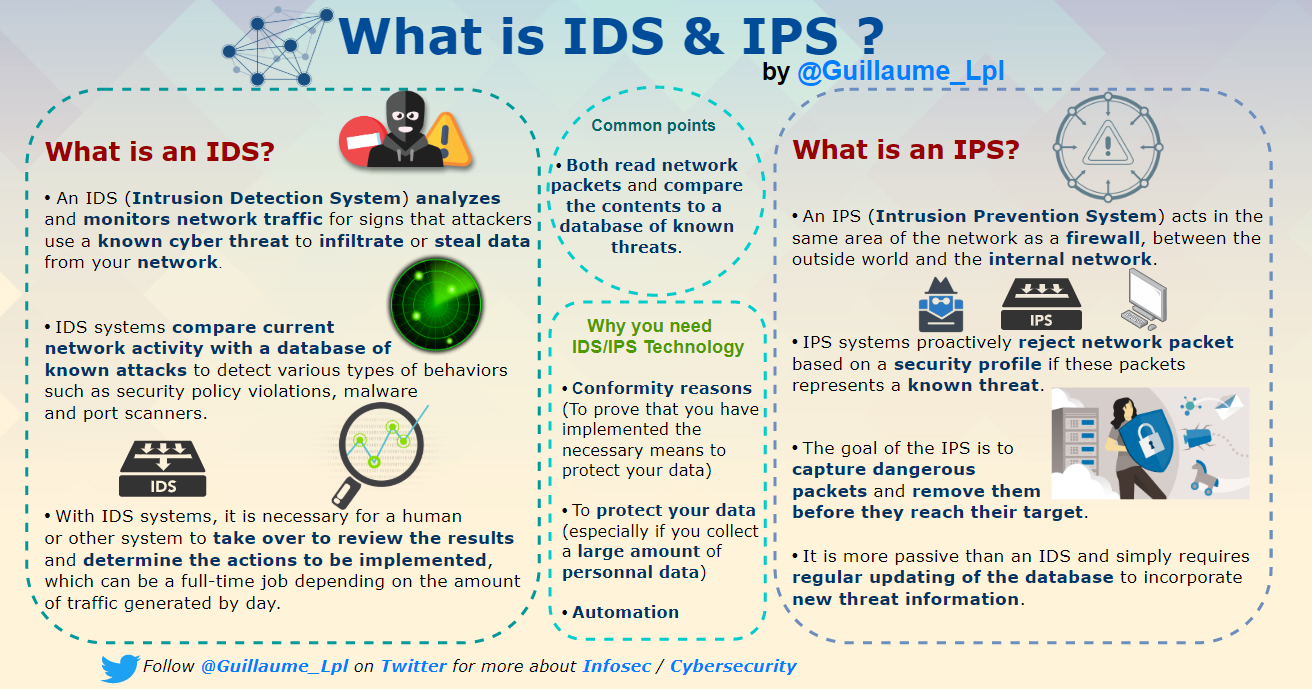
- What is IDS & IPS?
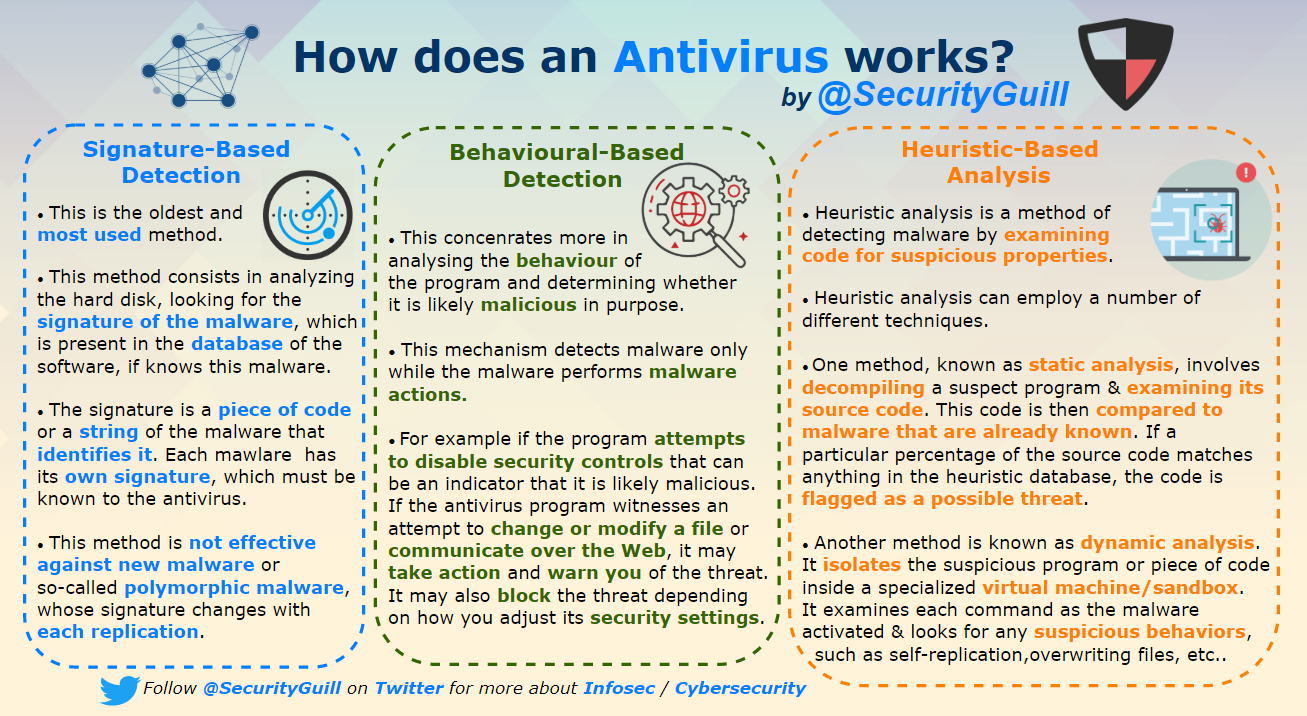
- How does an Antivirus works?
- What is a Botnet & How it works?
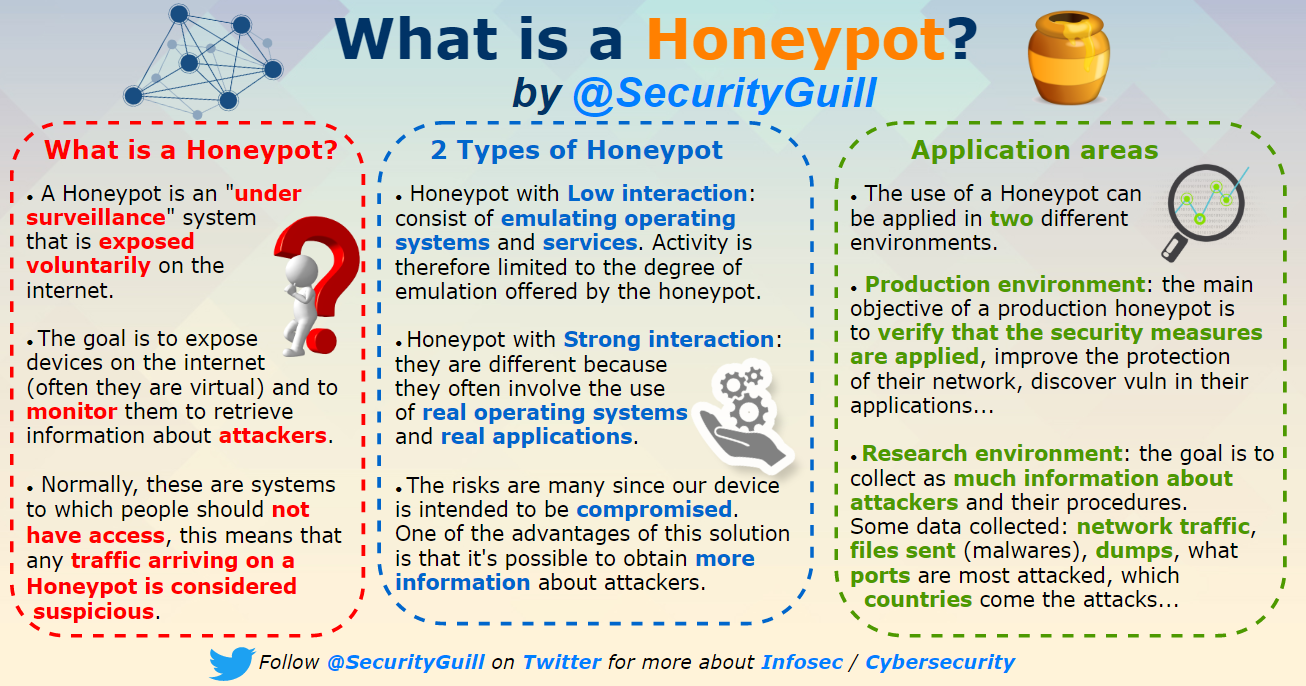
- What is a Honeypot ?
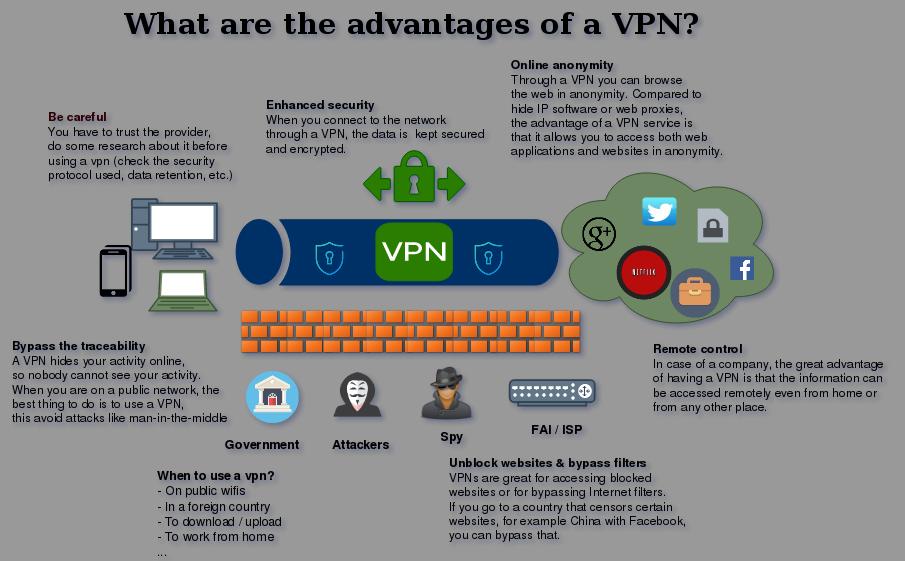
- What are the advantages of a VPN ?
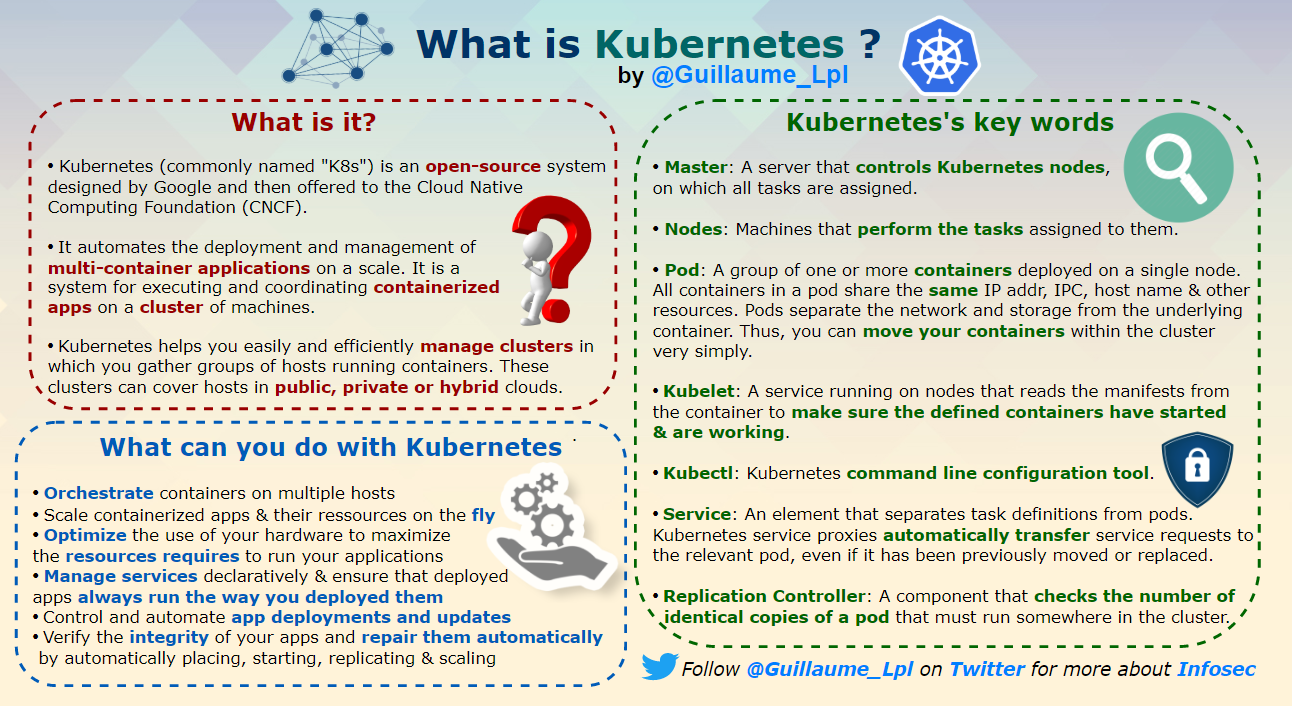
- What is Kubernetes?
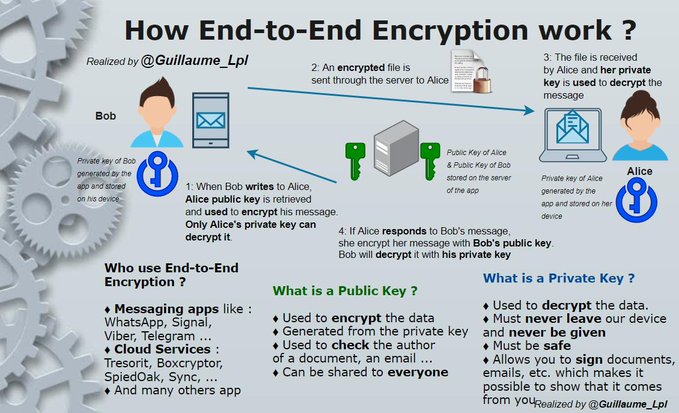
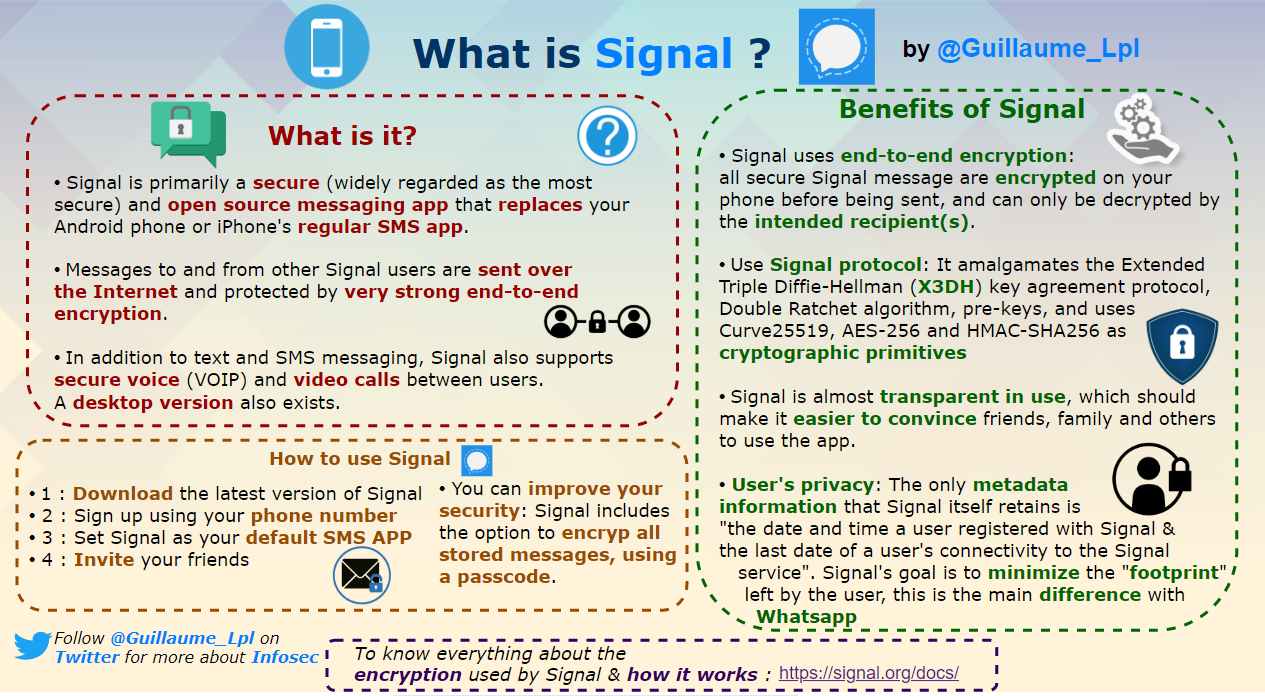
- What is Signal?
Protocols
Attacks
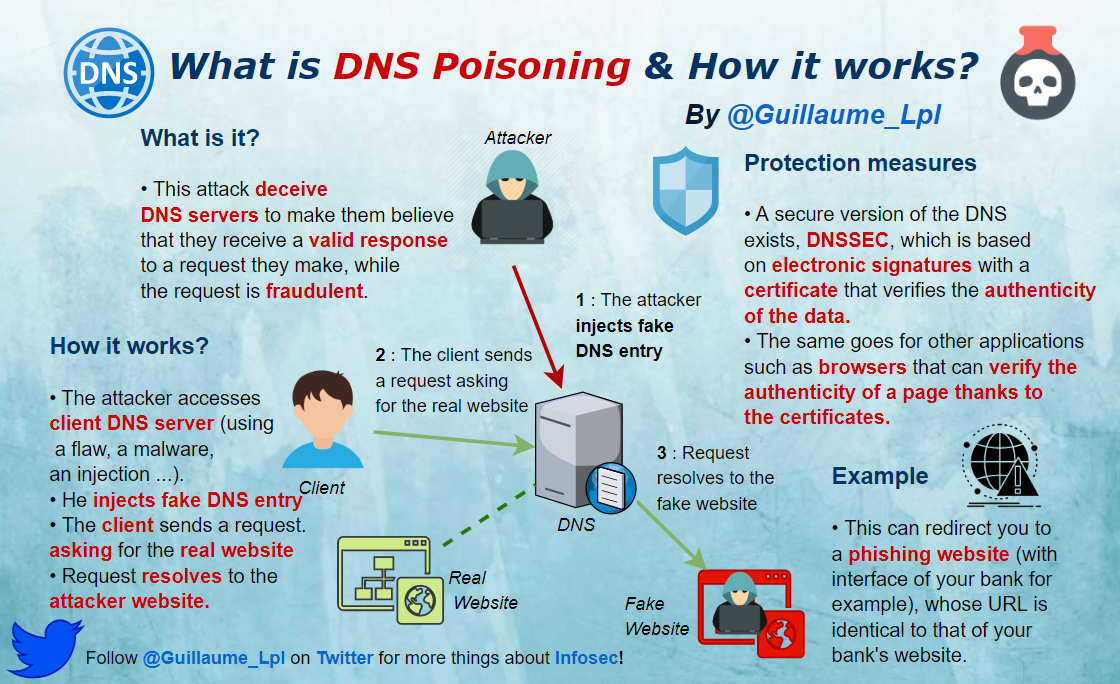
- What is DNS Poisoning & How it works?
- What is XSS Attack?
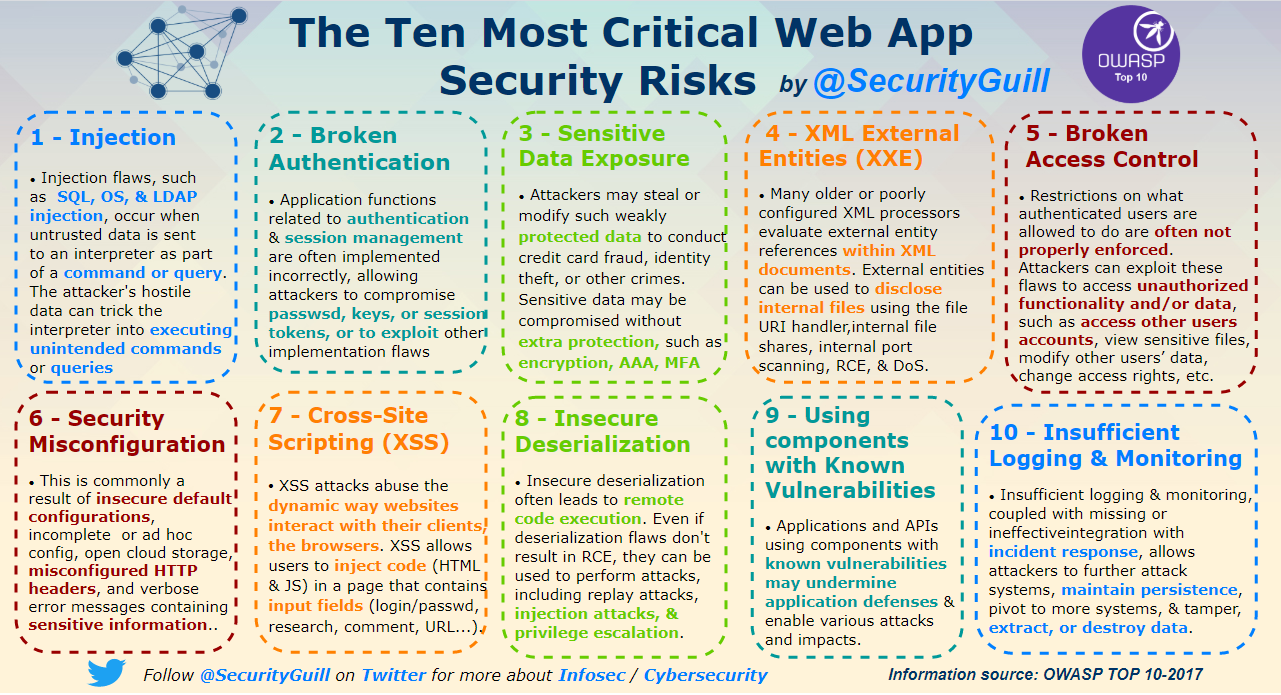
- The Ten Most Critical Web APP Security Risks
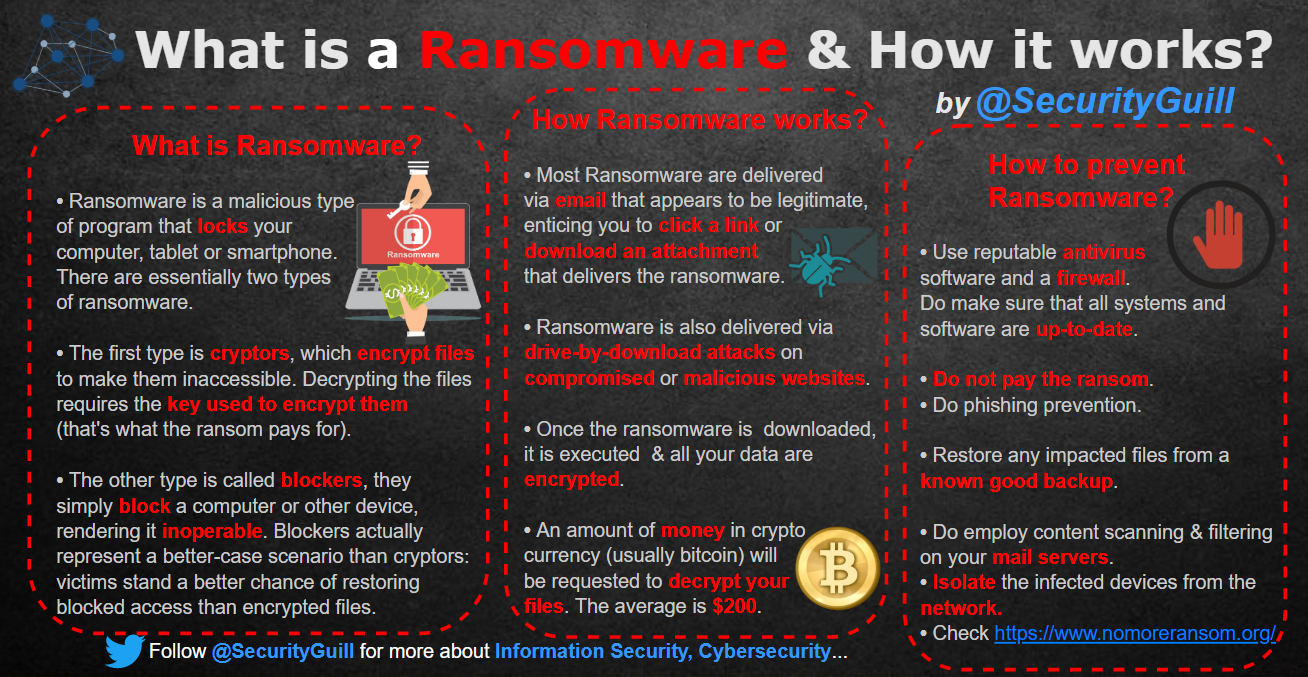
- What is a Ransomware and How it works?
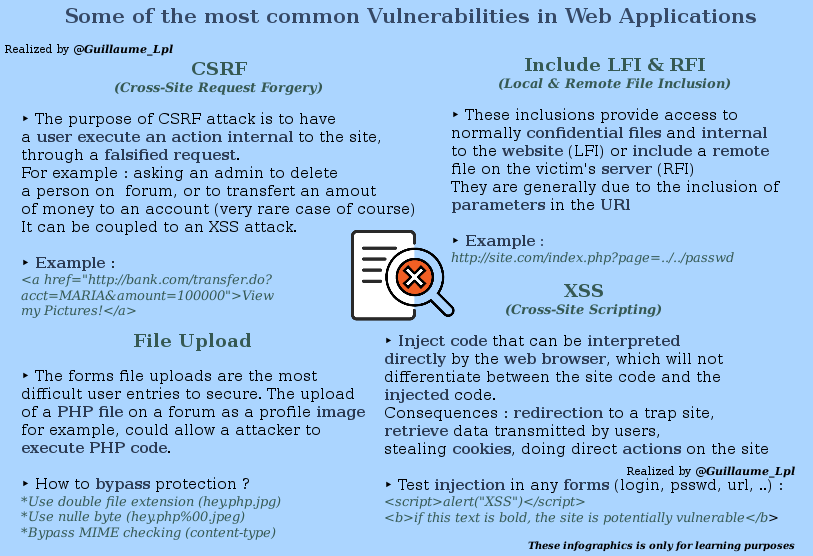
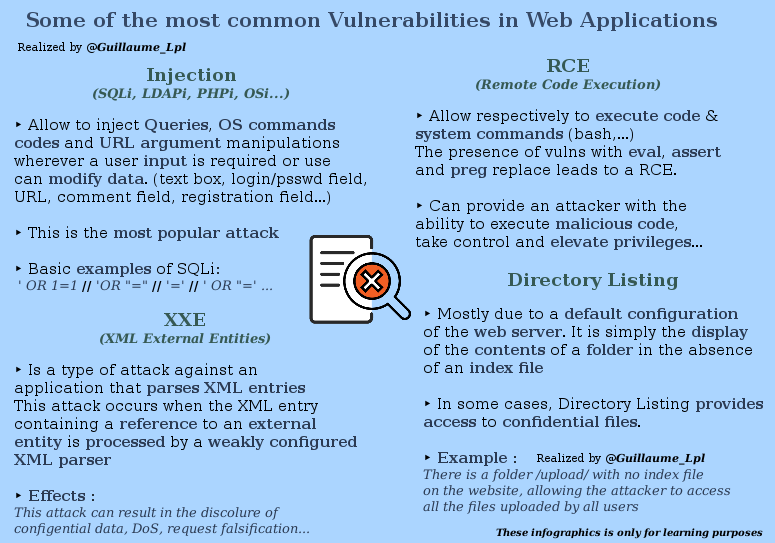
- Web Vulnerabilities
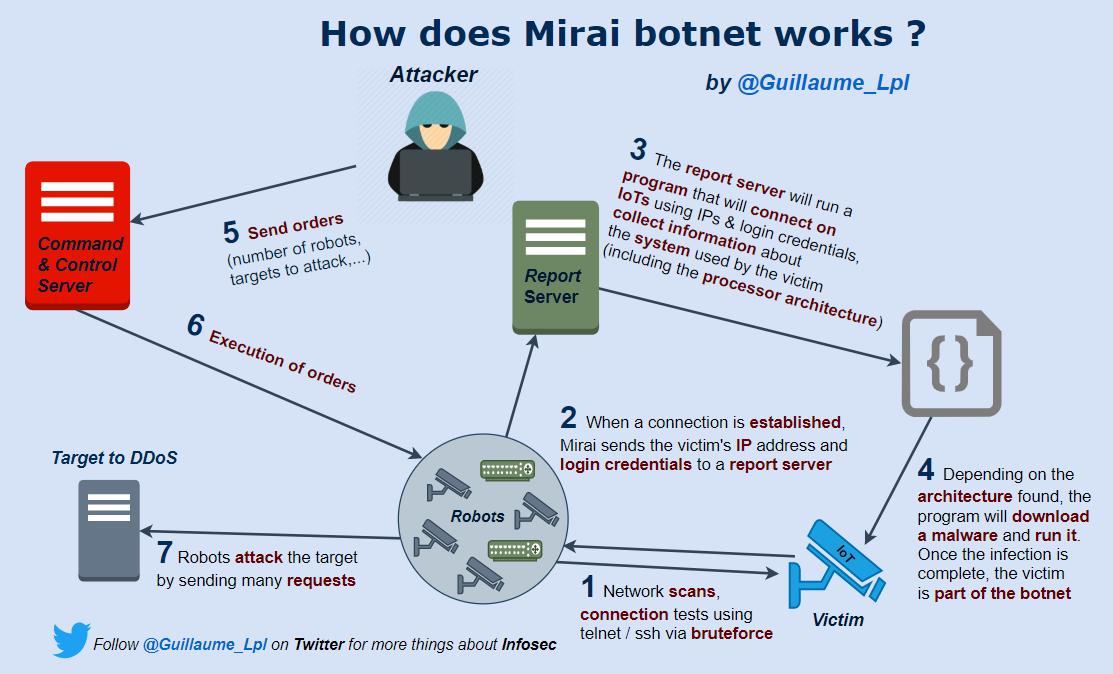
- How does Mirai botnet works?
- 5 most notorious Cyber Attacks
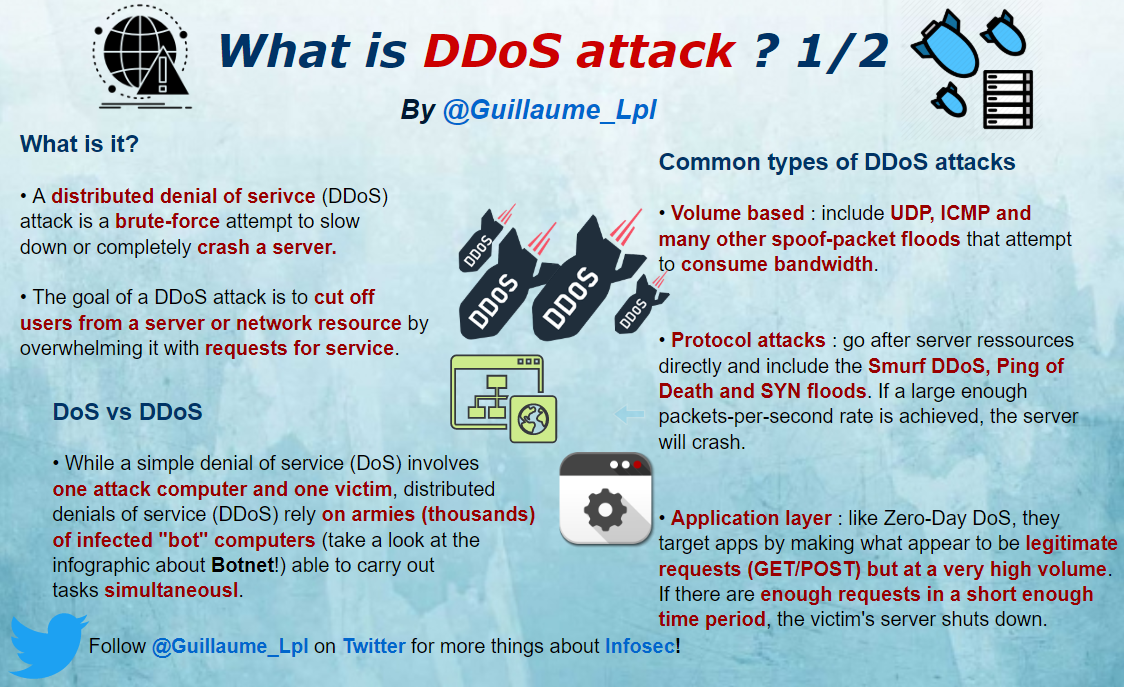
- What DDoS Attacks is?
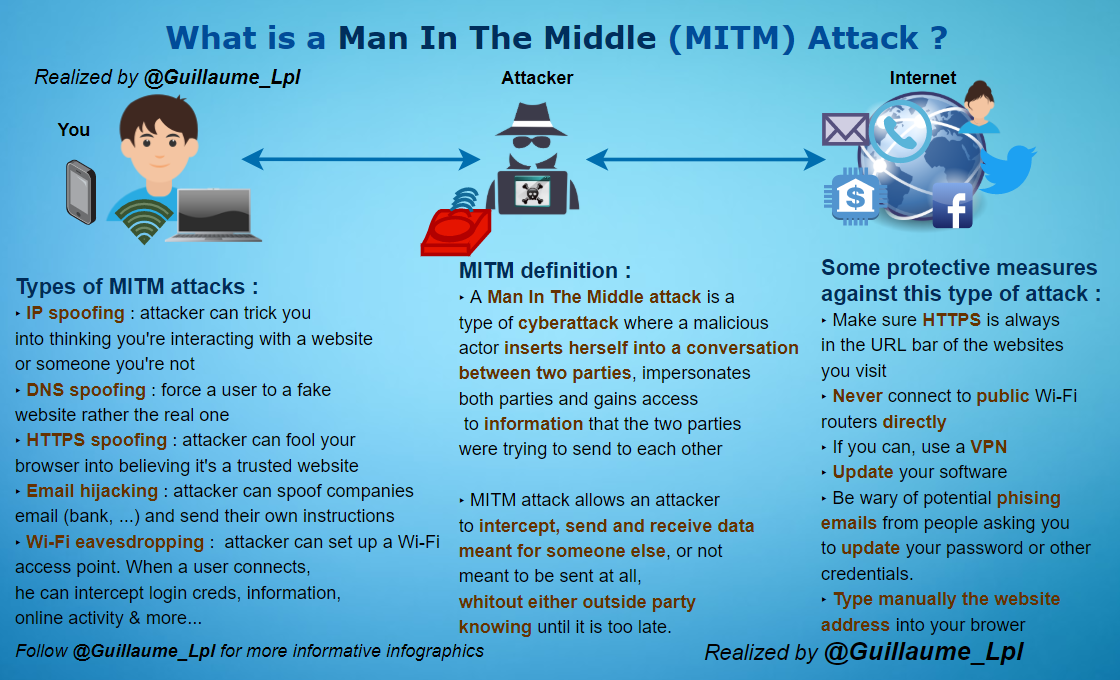
- What is Man-in-the-Middle attack?
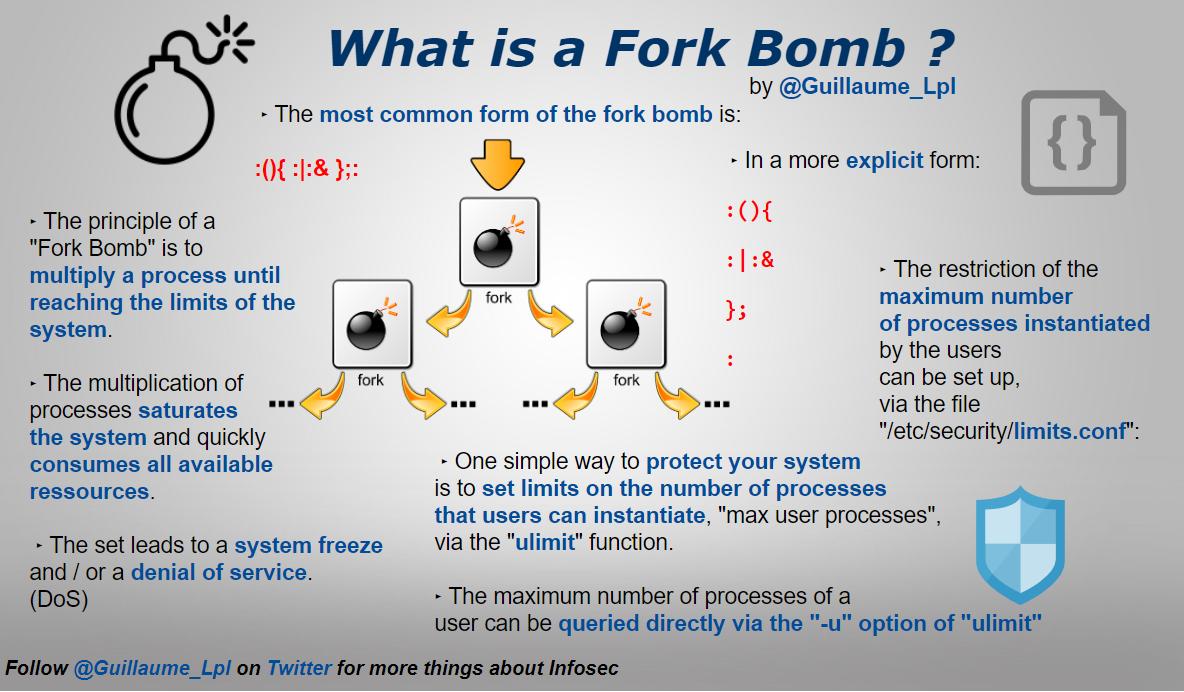
- What is a Fork Bomb?
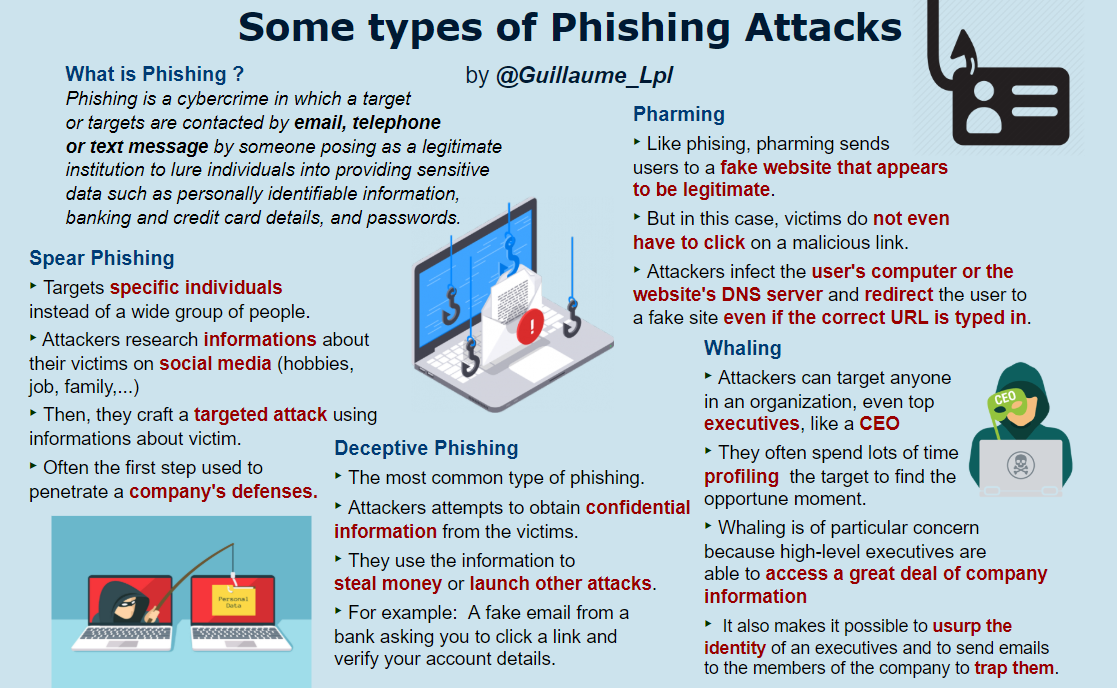
- Some types of Phishing attacks
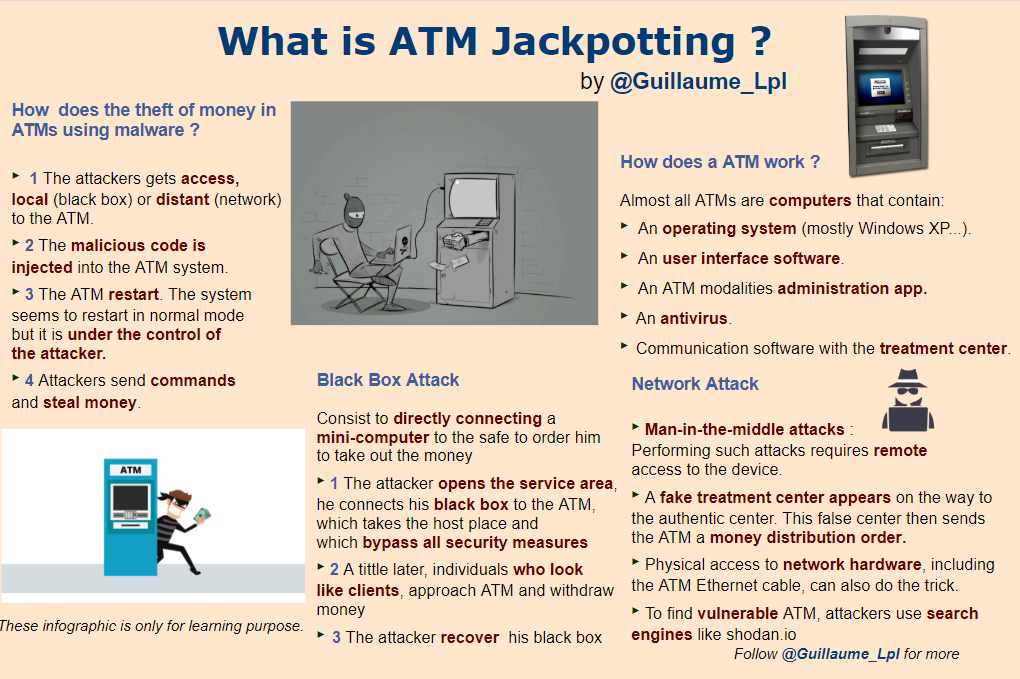
- What is Jackpotting Attack?
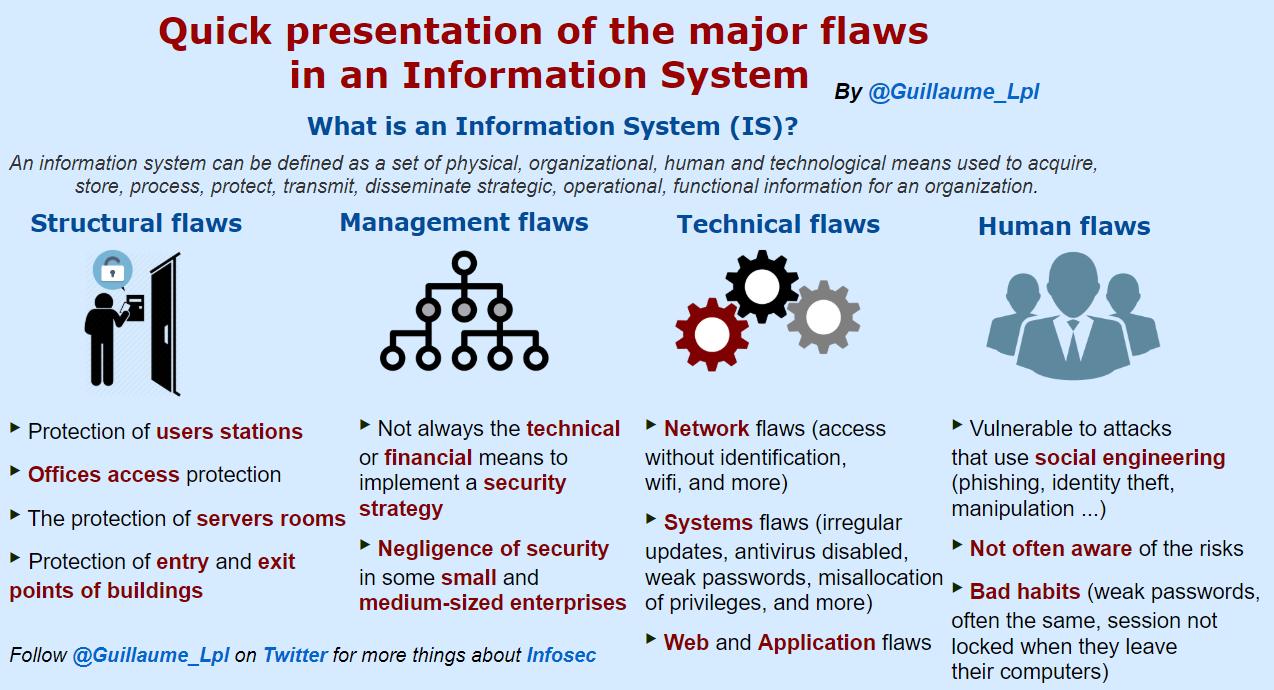
- The major flaws in an Information System
Tools
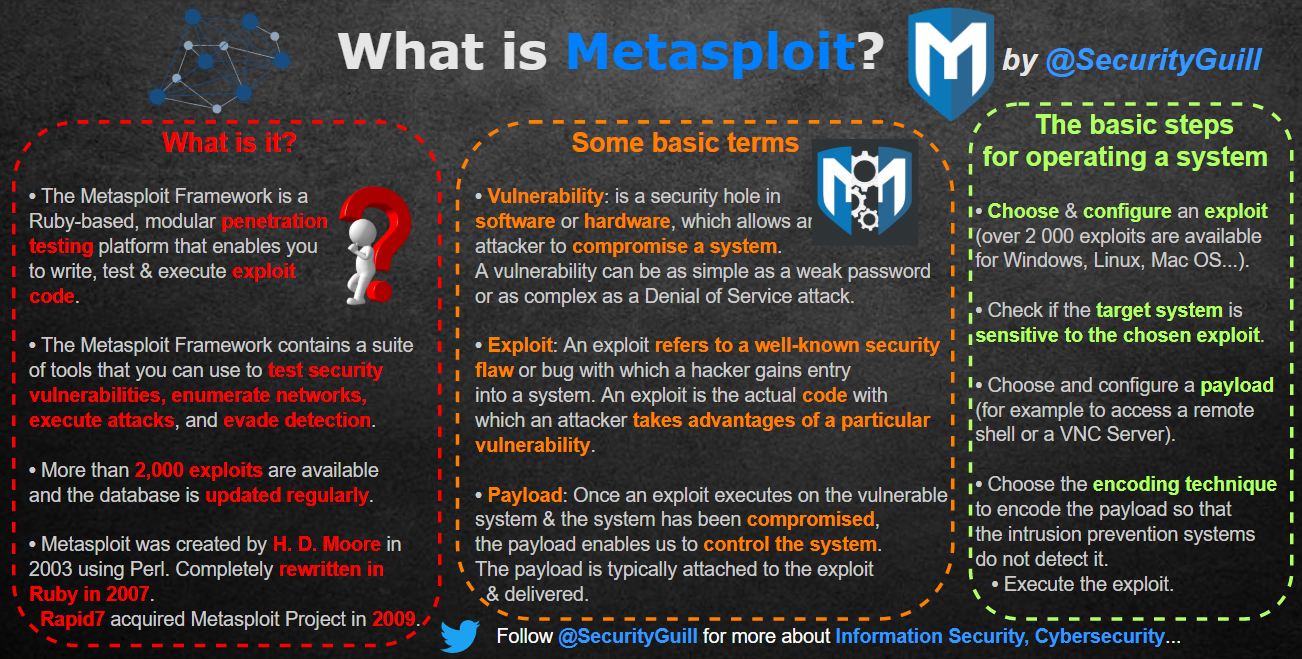
- What is Metasploit?
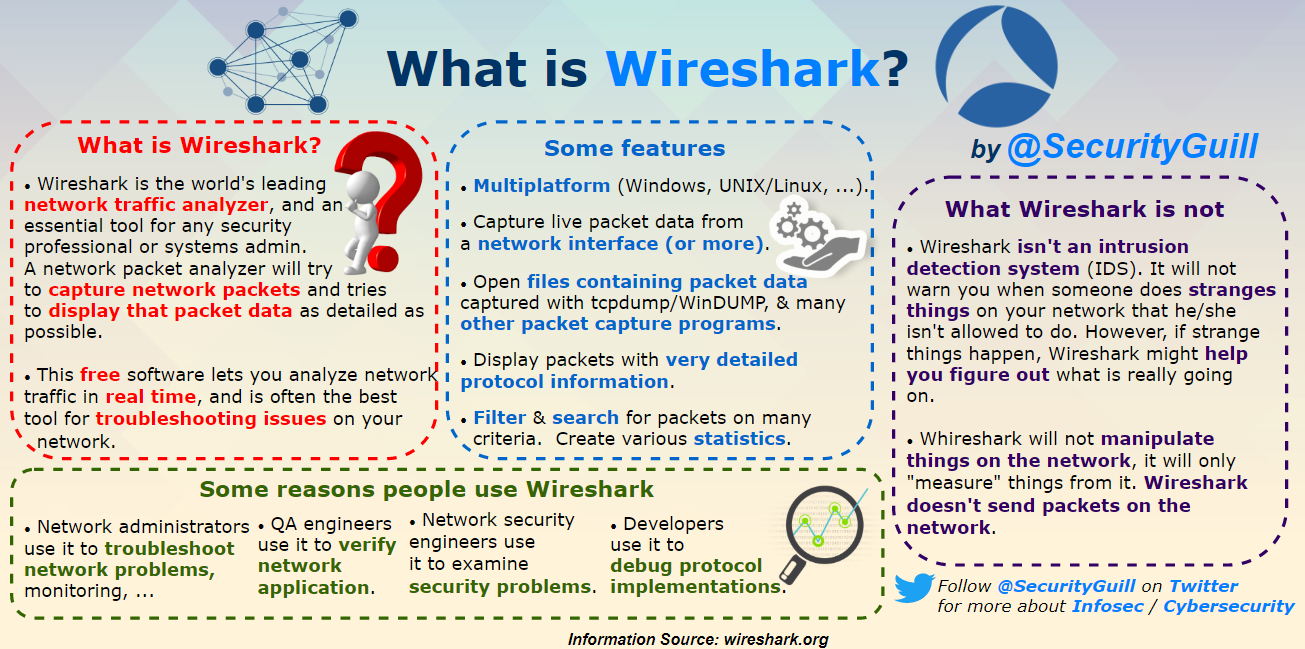
- What is Wireshark?
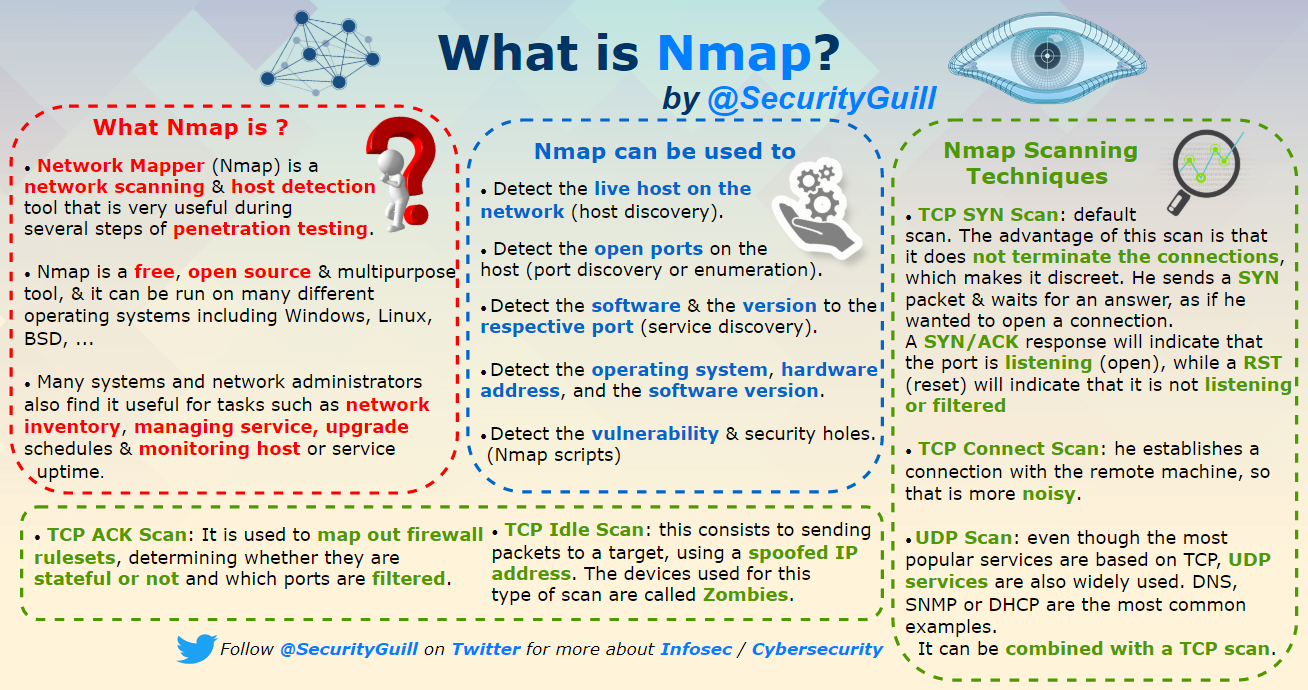
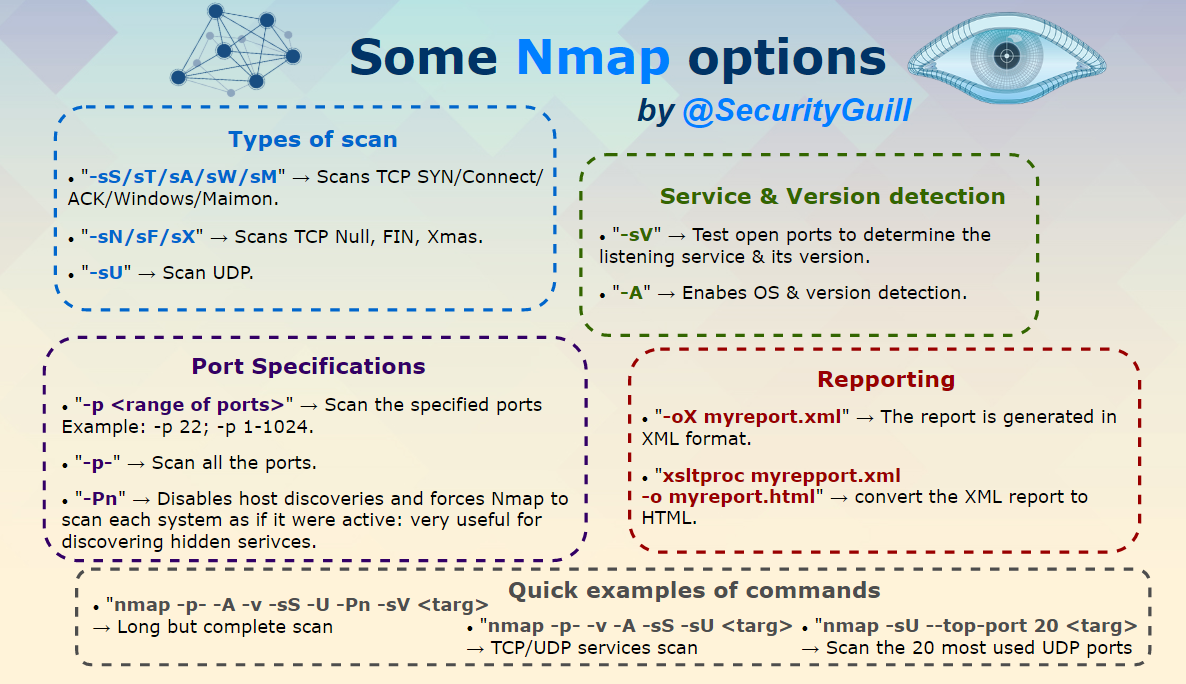
- What is Nmap?
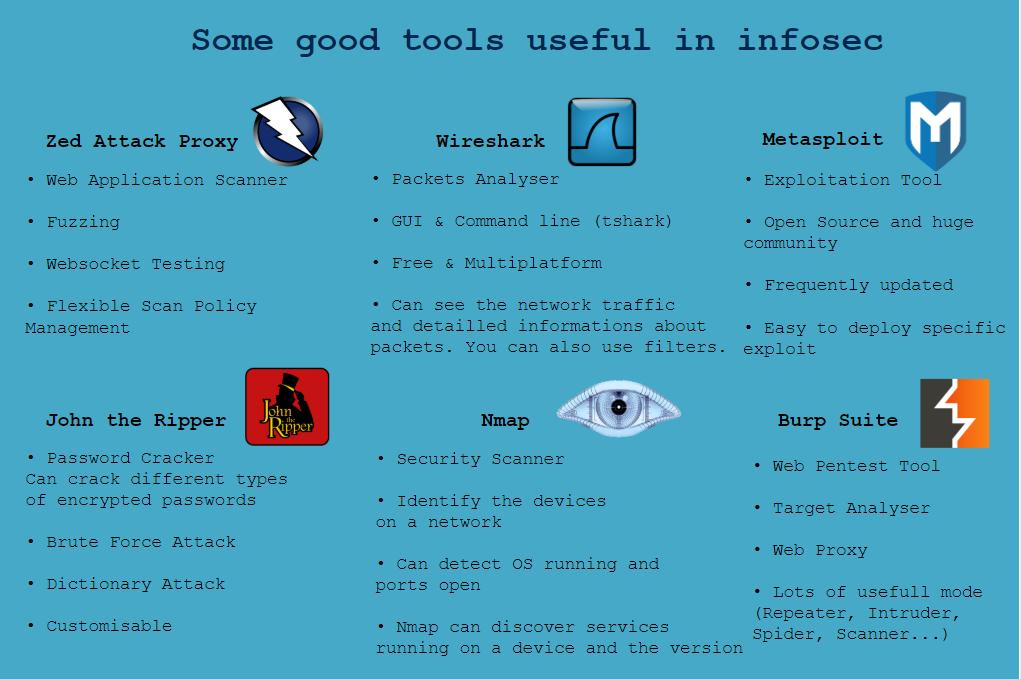
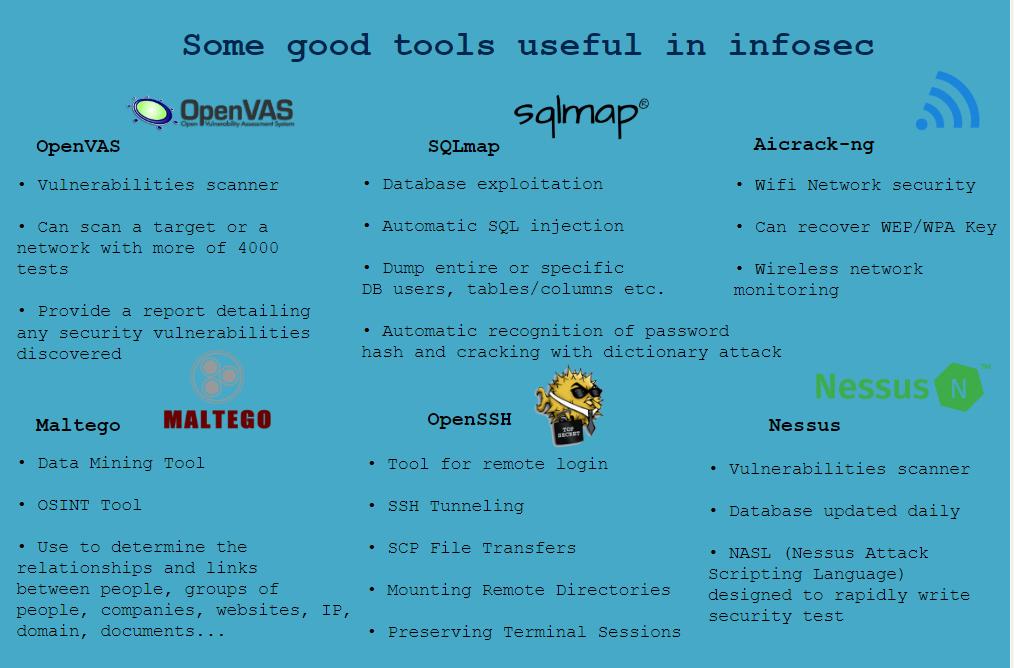
- The most useds tools in Infosec
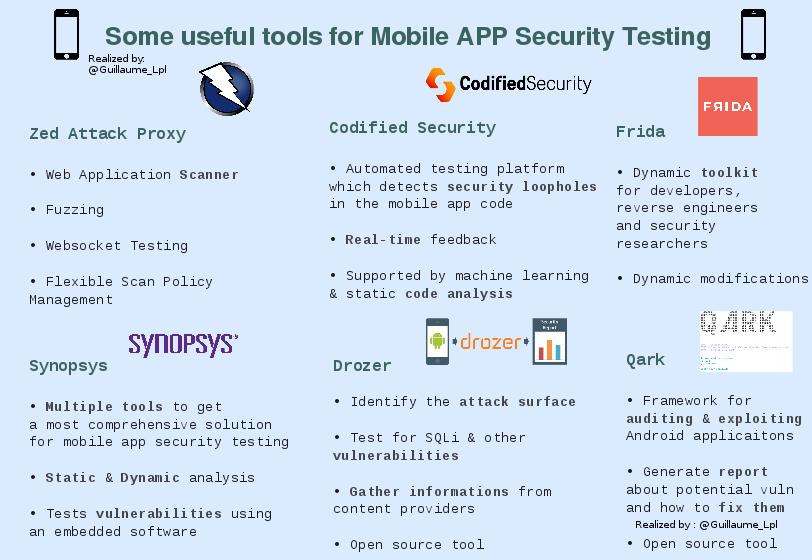
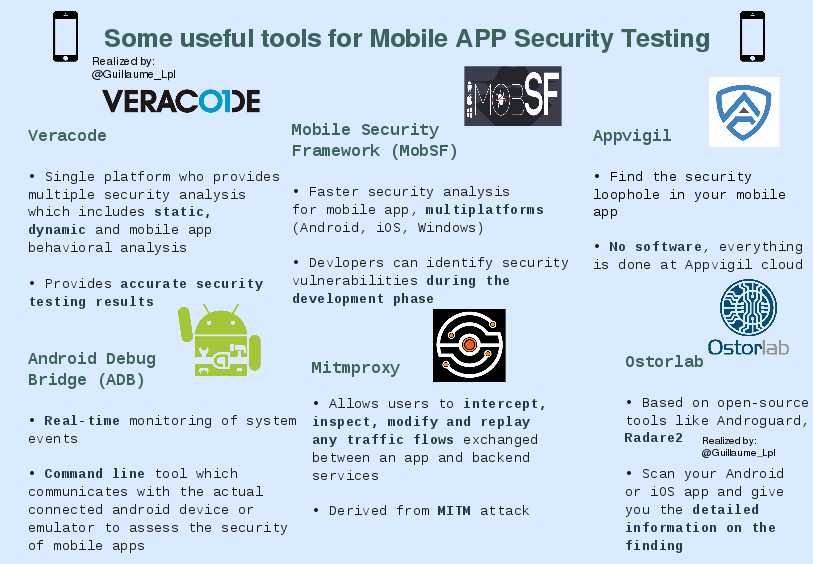
- Some good tools useds for Mobile APP Security testing
- Some good tools useds for OSINT
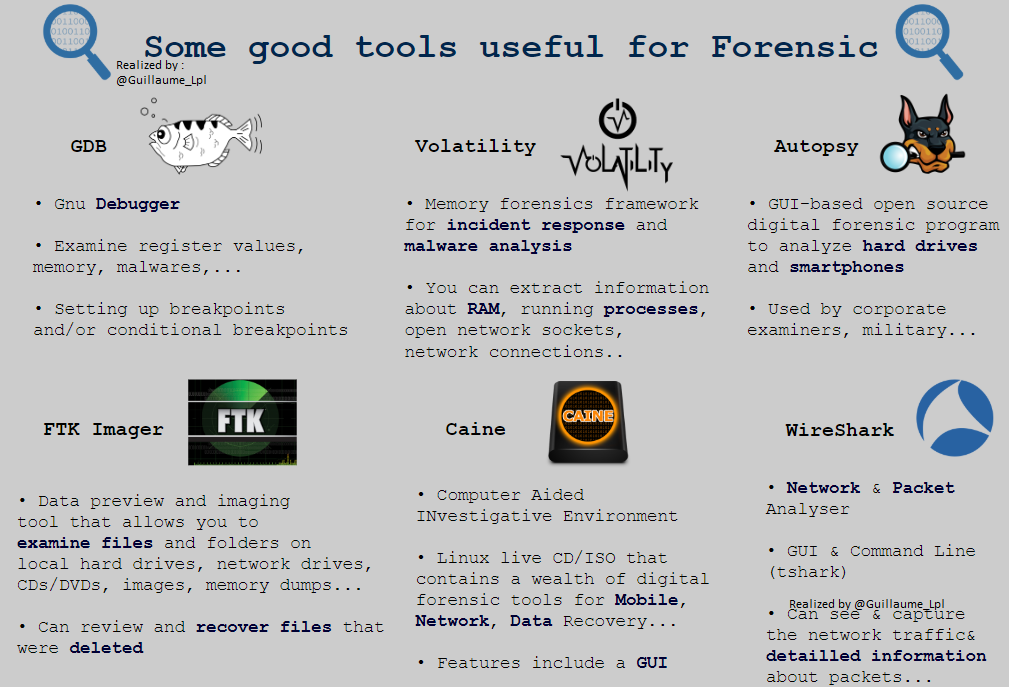
- Some good tools useds for Forensic Analysis
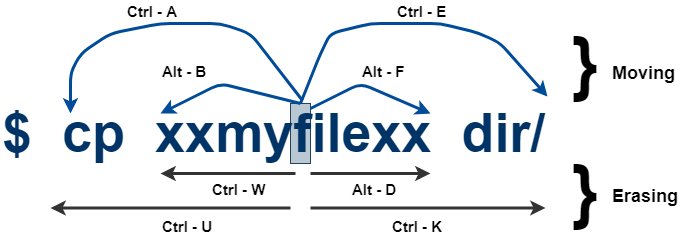
- Shortcuts for Linux terminal
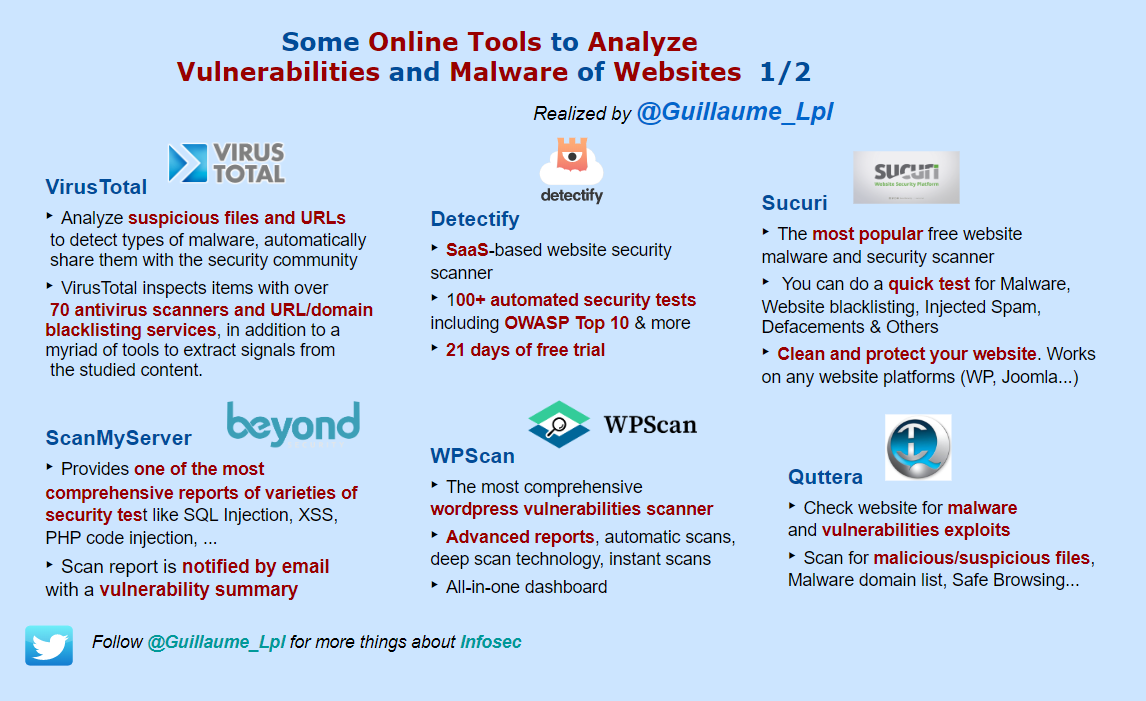
- Some Online Tools to Analyze Vulns and Malware of Websites
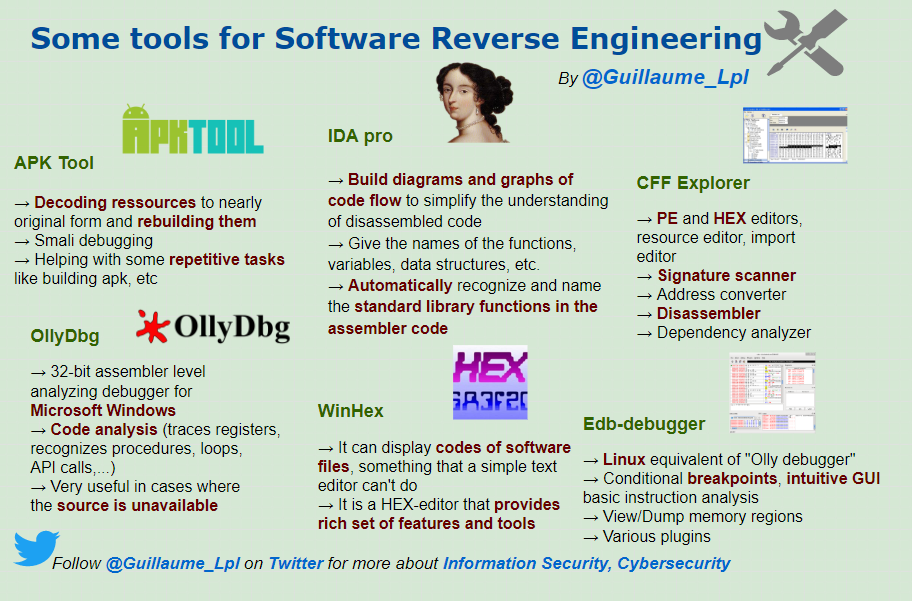
- Some tools for Software Reverse Engineering
Terms
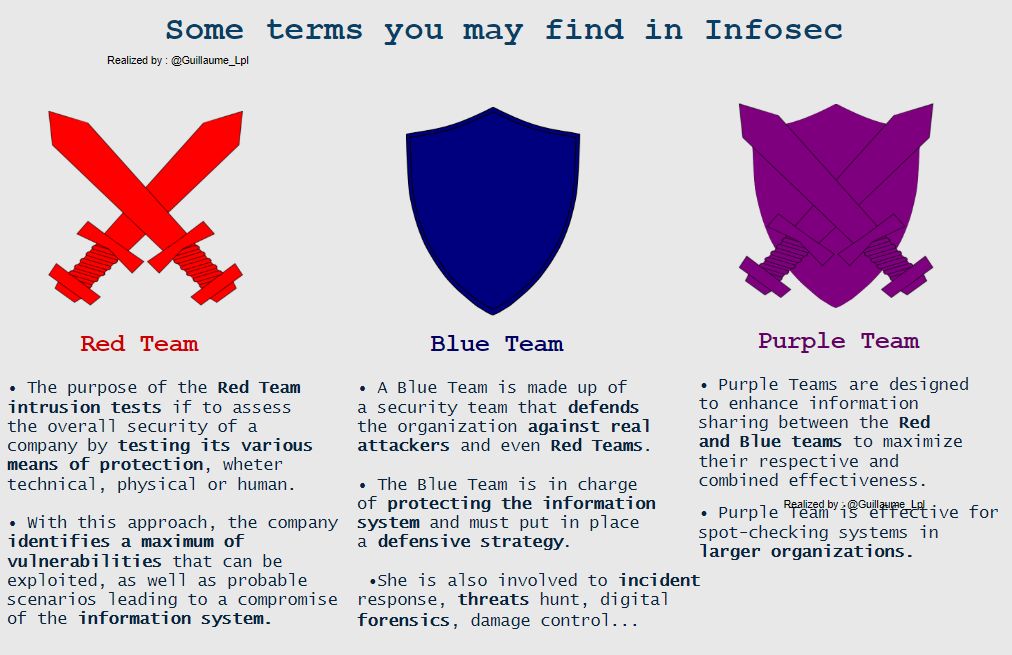
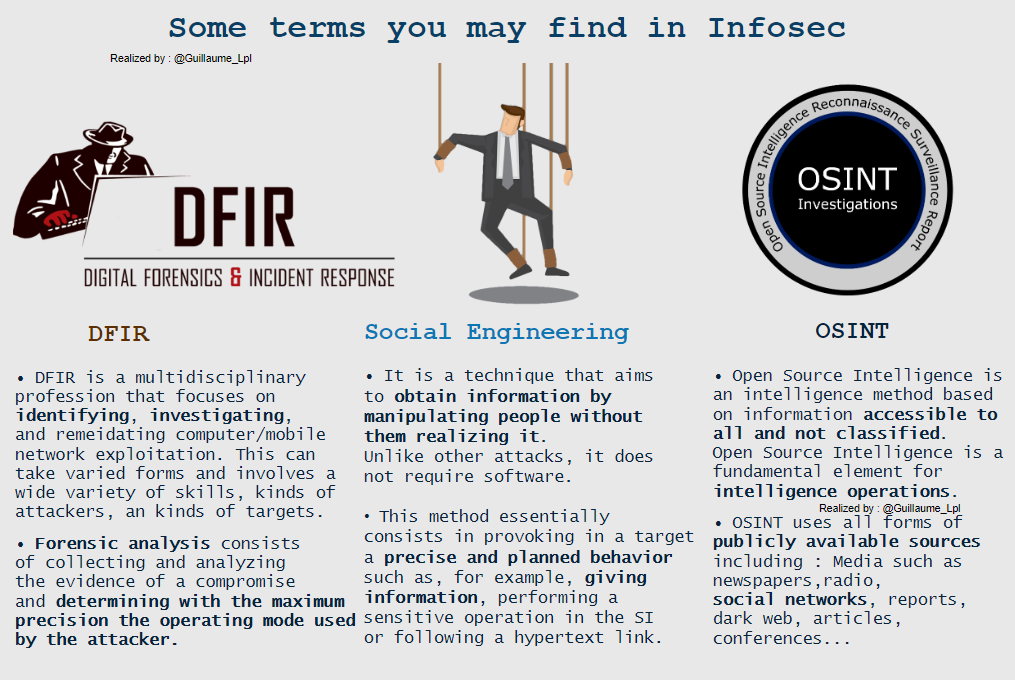
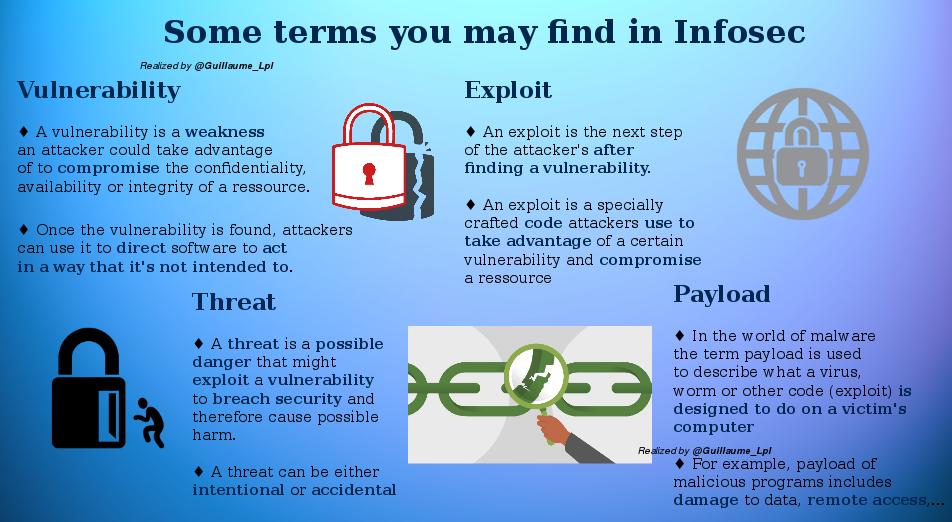
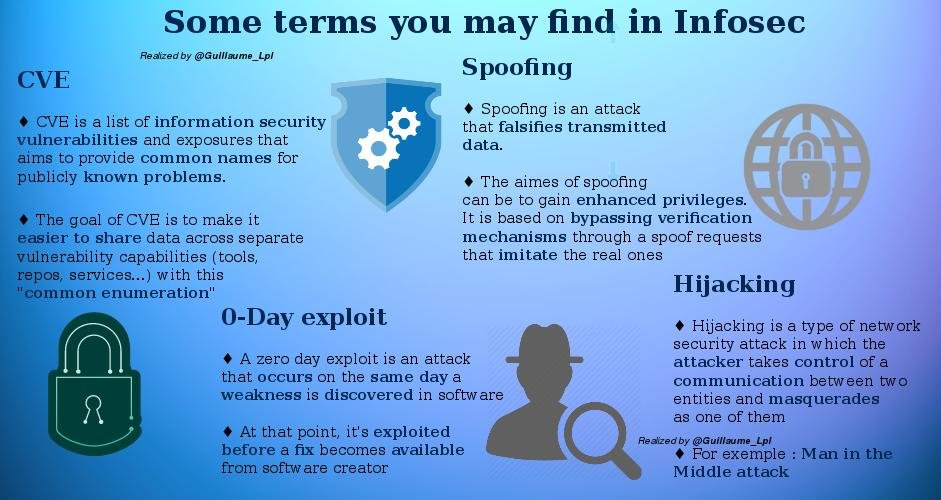
- Some terms used in Infosec
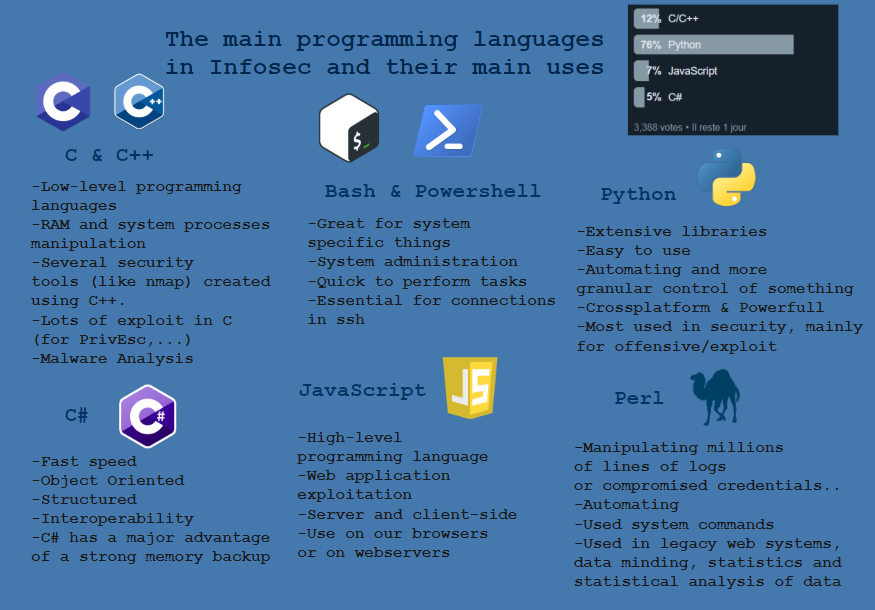
- The main programming languages in Infosec and their main uses
- Some good practices to avoid social engineering attack
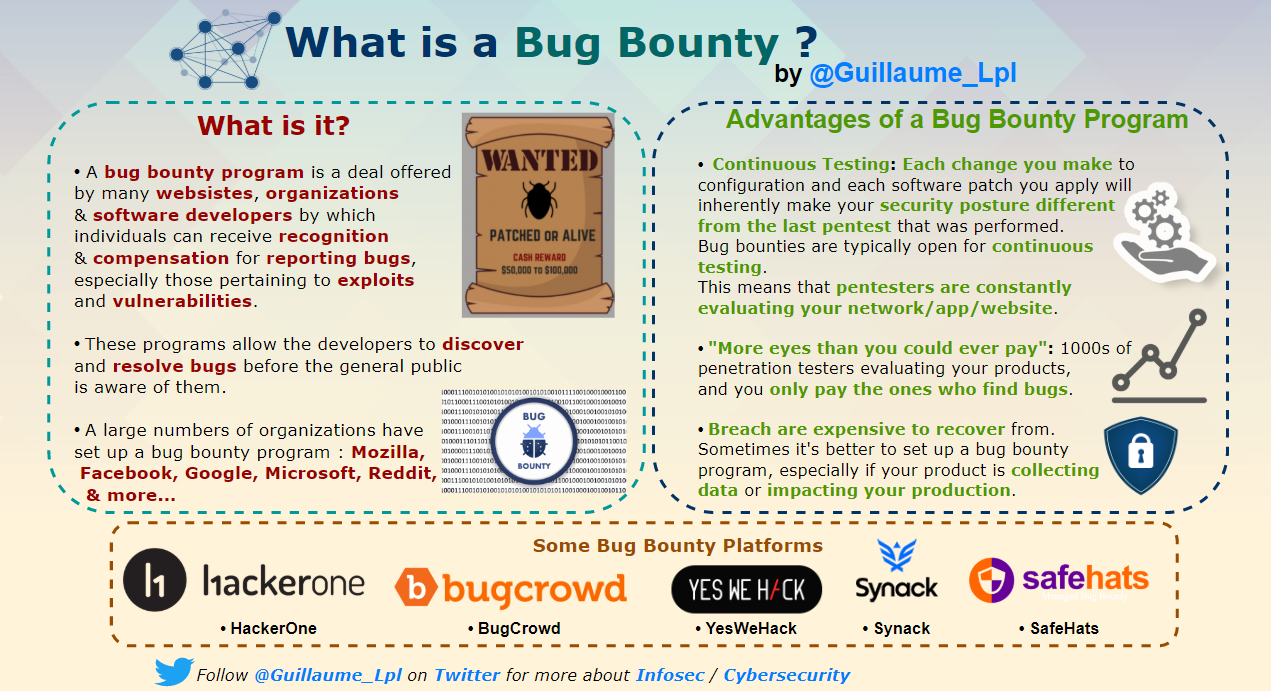
- What is Bug Bounty?
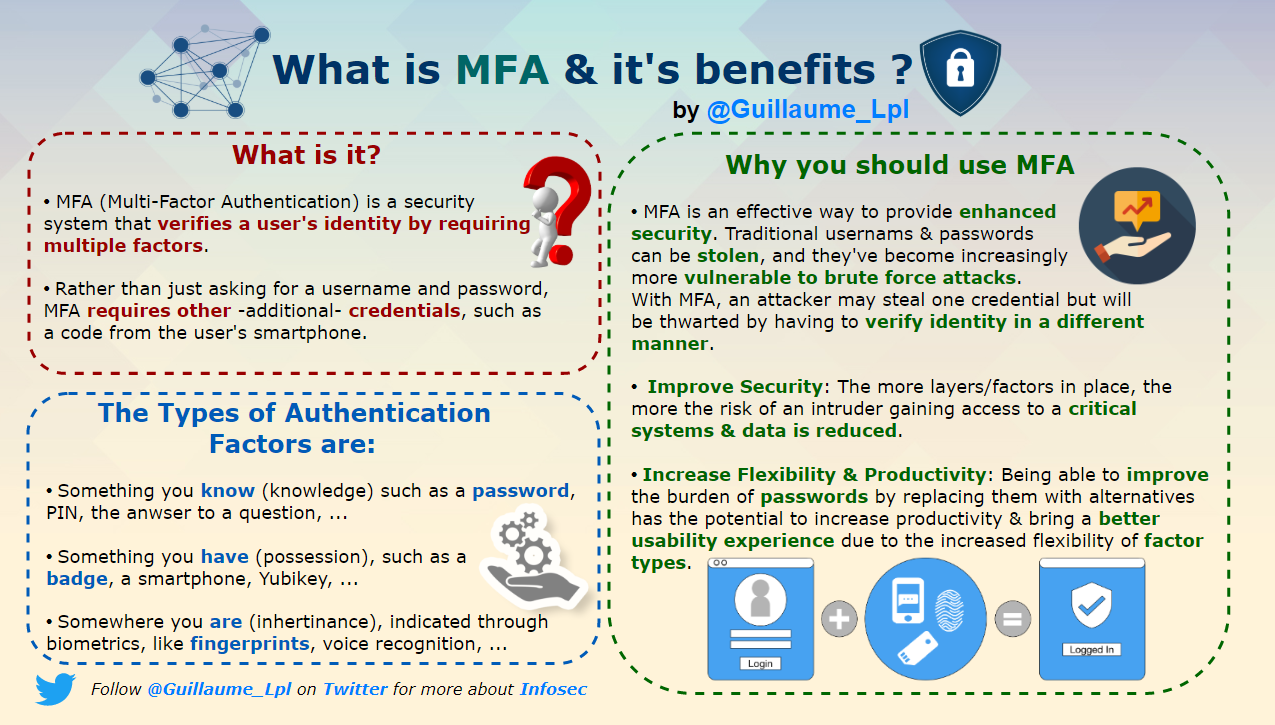
- What is Multi-Factor Authentication?
Download
Download
Download
Download
Download
Download
Download
Download
Some good practices to avoid social engineering attack
Download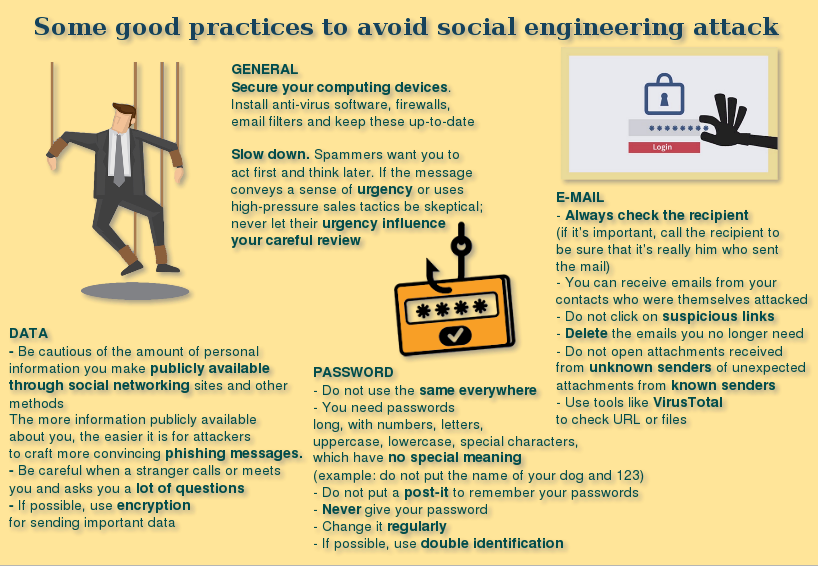
I also did an article on this topic if you want to learn more, HERE
5 most notorious Cyber Attacks
Download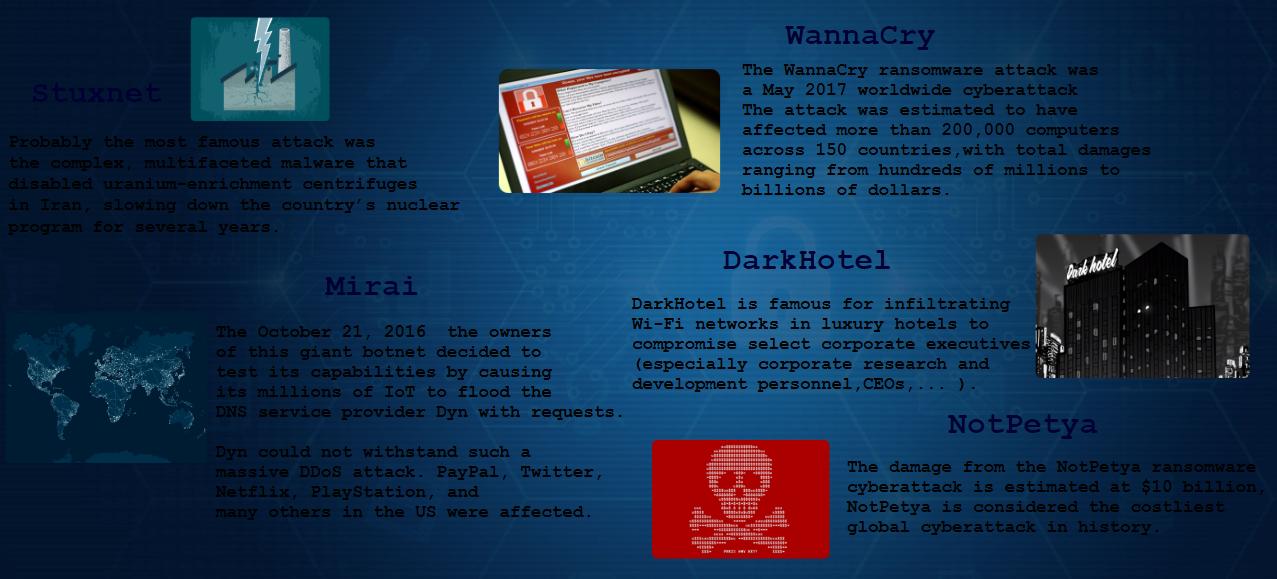
I also did an article on this topic if you want to learn more, HERE
What is Bug Bounty?
Download