Index
- What is social engineering ?
- How is a social engineering attack ?
- Examples of known attacks
- How to protect yourself from this type of attack?
- End of this article
Information system: An information system can be defined as a set of physical, organizational, human and technological means implemented to acquire, store, process, protect, transmit, disseminate information to strategic, operational or functional character for an organization.
In an information system, there are often four categories of flaws:
In this chapter we will focus on the human fault, which in my opinion is the most dangerous.
What is social engineering ?
It is a technique that aims to obtain information by manipulating people without them realizing it. Unlike other attacks, it does not require software.
This method essentially consists in provoking in a target a precise and planned behavior such as, for example, giving information, performing a sensitive operation in the SI or following a hypertext link.
To achieve this, the attacker will not hesitate to play with your emotions, find your weak points, adapt his behavior according to your reactions ... all this without you realizing it.
How is a social engineering attack ?
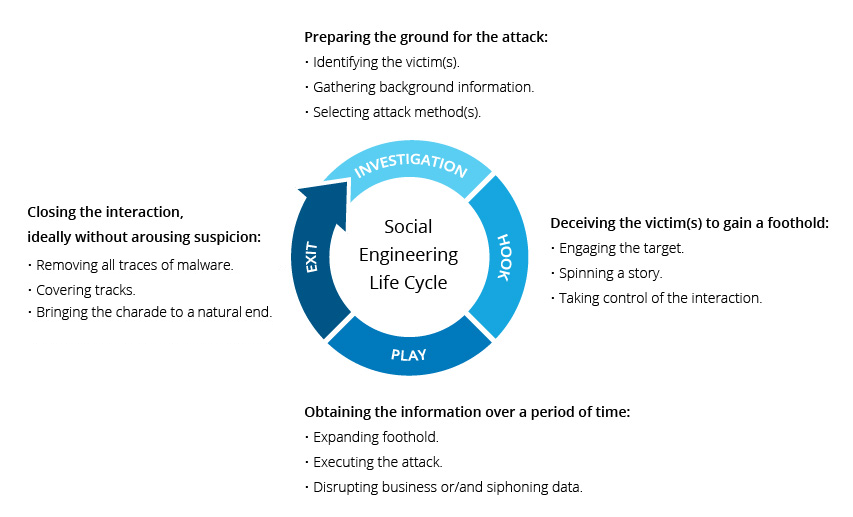
Source : https://www.incapsula.com/web-application-security/social-engineering-attack.html
The goals of the attacker can be multiple: he can do that to have fun, to hurt you personally, but often it is to target your business and abuse your trust, because you are not without knowing that users are the main flaw of an information system.
In general, only one person at a time is targeted.
At first, the goal of the person who will perform this type of attack, is to collect as much information about you as possible. To do this, Google is his best friend. The first information that the attacker will look for, it will be a way to contact you: an e-mail address, a mobile phone number, a home address ...
He will then establish a list of all the information he finds on you, and even on your loved ones: your age, your activities, your business, your favorite football team, your clothing preferences, ...
All the information you make available to social networks can be useful to the attacker, that's why he will not hesitate to look carefully at your profiles Facebook, Instagram, Linkedin, Twitter ..., which are a mine of immense information. Nowadays, most people are registered on a social network.
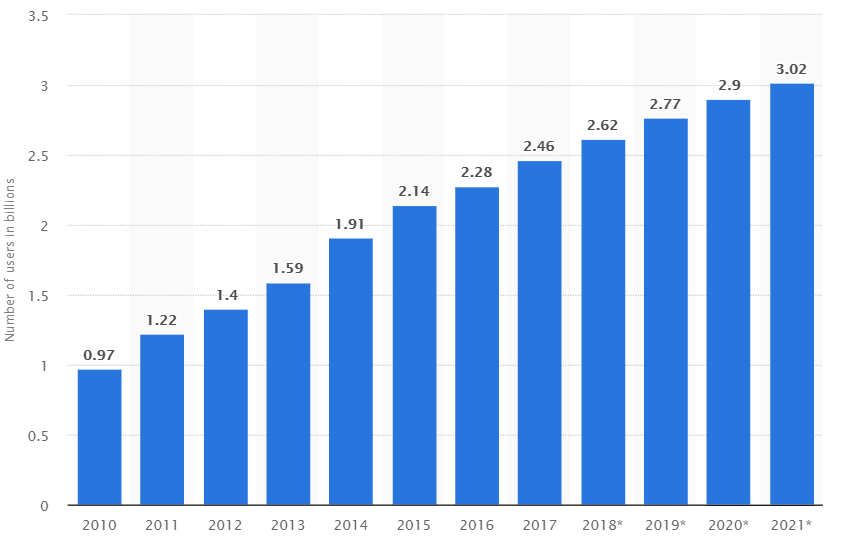
Source : https://www.statista.com/statistics/
278414/number-of-worldwide-social-network-users/
This statistic shows the number of social media users worldwide from 2010 to 2016 with projections until 2021. In 2019, it is estimated that there will be around 2.77 billion social media users around the globe.
In a second phase, the attacker will sort the information he has collected about you, and then try to link this information.
A small example: The attacker knows that you are registered on a cancer site and that you have made a donation, and he also knows that your sister was hospitalized following your last Facebook post, or that of your loved ones died as a result of this illness, having seen a death notice on a newspaper.
He can quickly conclude that you are sensitive to this.
The next phase will consist in preparing his attack, if he has relevant information, and he has managed to draw links between them, he will be able to organize the course of his attack: choose for whom is- what is going to happen, by what means will he contact you, what will be the main subject ...
But he will also prepare a speech to be as credible as possible during the conversation, and prepare answers to questions you could ask him, by imagining several scenarios.

Source : http://www.associationeconomienumerique.fr/
trois-vecteurs-de-social-engineering-2017/
Finally, when his attack is ready, he will only have to implement it. He will contact you (by email, by SMS, by phone call, by letter, or even face to face).
If we go back to the previous example, it could for example send you an e-mail posing as the president of the cancer control association that you support, to thank you for your loyalty, or you send a document (trapped) to fill in for X reason.
What is important to know is that an attacker will not necessarily go on the attack of the first exchange with you. He could use it to get closer to you, to obtain other information, to gain your confidence ..
Examples of known attacks
Of course, the attack scenarios are multiple, a good attacker will adapt to any situation, in front of anyone.
These very well explained examples come from the site https://www.institut-pandore.com/
Here are some examples of known attacks that have been made:
First case: Netragard
Netragard is specialized in IT security auditing. In other words, it is paid by its customers to try to hack them by any means. The goal: to check the flaws of a company.
When Netragard's boss was hired by his client this time, he knew he would have to be trickier than ever. The client company has been paying close attention to its safety for years.
His idea: tinkering with a computer mouse to integrate a spyware capable of taking control of the computer on which the device is connected, without the knowledge of the user obviously.

The attack is extremely sophisticated from a computer point of view. But its peculiarity and genius rests mainly on its social engineering aspect.
To use the rigged mouse within the client company, Netragard hackers had to do extensive research on each employee in the box.
Facebook, Linkedin ... profiles: everything has been scrutinized. Finally, Netragard's boss decided to send the mouse to a particular employee, who seemed more likely to fall into the panel, the modified mouse was sent to this employee in the form of a "gift".
Eventually, the employee in question plugged in his mouse within a few days of receiving it, and the company took control of the computer.
Second case: Hadnagy
Again, this story is about a security audit company that has come up with a great plan to hack the company that hired it. The CEO warned: "It will be impossible to hack me" he was sure and certain.
Hadnagy, the hacker in charge of testing the security of the box, told the press: "The boss imagined that someone was going to phone him to ask for his password or something like that ... he was getting ready for something in genre."
To get started, Hadnagy began looking for the location of the company's servers, server IP addresses, employee emails, phone numbers, employee names and titles, and more. But the big-lot was elsewhere: the hacker discovered that a family member of the CEO had fought against cancer, and had survived.
As a result, the boss had moved closer to a foundation involved in cancer research. Meanwhile, the hacker also discovered the favorite restaurant and the favorite football team of the CEO.
With all this information, he was ready to hit. He called the boss pretending to be the foundation to which he had been interested in the past. He informed her that the foundation was organizing a lottery in exchange for a donation and that one of the prizes was a place for a football game in which her favorite team was participating ... There were other hypothetical lots, such as ... an evening offered in various restaurants, including his favorite!

Source: https://www.slpowers.com/social-engineering-phone-
impersonation-testing
The boss seemed very interested. Hadnagy asked him his e-mail address to send him a PDF of registration. Everything was going smoothly. The hacker could even ask the CEO what version of Adobe Reader he was using "to be sure he was seeing the document properly".
Where is the trap ? The registration PDF for the lottery was obviously trapped. Adobe Reader is a true strainer (as evidenced by the millions of almost daily updates imposed on us by Adobe on Windows). The case was in the bag: the hacker had control of the boss's PC.
Third case: Journalist
An American journalist was hacked "from A to Z" all his Apple devices, his email account, his data storage accounts and his Amazon account. The hacking at the origin of the attack did not use any "technical" means to achieve this. How did he do it?
Step one: Call Amazon customer service pretending to be Mat Honan, the journalist who was the victim of the attack. The pirate's strategy is ingenious to the possible. During his first call to Amazon, he asks to add a credit card to his account. This is a classic procedure that Amazon agrees to honor by phone. Just give his name, his address and the code of his credit card.
Second step: the hacker recalls Amazon but this time, he explains that he lost access to his account. Guess what Amazon requires to verify the identity of the caller? The last 4 digits of a credit card associated with the account .... the hacker simply gave the last 4 digits of the card he had just added. At this point, the hacker was given full access to the journalist's Amazon account.

Third step: get access to the victim's iCloud account. Access to this account gives you immediate access to your iPhone, MacBookAir, Twitter account and Gmail account (which is the backup account). It could not be easier.
When resetting the IDs of an iCloud account, Apple only asks for 3 pieces of information: the account email, a billing address, and the last 4 digits of the credit card associated with the account. Remember, the hacker had just gained full access to his victim's Amazon account. He had access to the last 4 digits of his real bank card at the same time.
Fourth step: hacking in good standing with deletion of all data.
Other examples:
How to protect yourself from this type of attack ?
Here are the main rules to reduce the surface of an attack type social engineering:

Source : https://www.zonealarm.com/
blog/2015/11/6-ways-to-avoid-social-engineering/
End of this article
Follow me on Twitter to be informed of my new articles/infographics →  (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with
Buy me a coffee