Index
- Introduction
- What is a Honeypot ?
- Honeypot with low interaction
- Honeypot with strong interaction
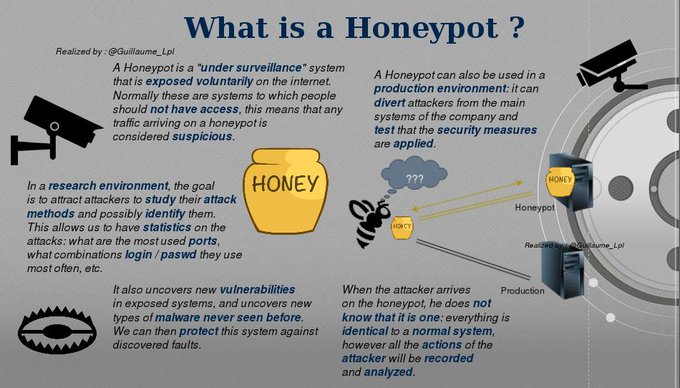
- Production environment
- Research environment
- Conclusion and Infographic
Introduction
In recent years, the Internet of Things has seen strong growth in the world of "everything connected".
We have more and more things that are connected to the Internet: our phones, our laptops, voice assistants, cameras, routers ... and this in different areas: health, social life, marketing, home automation ...
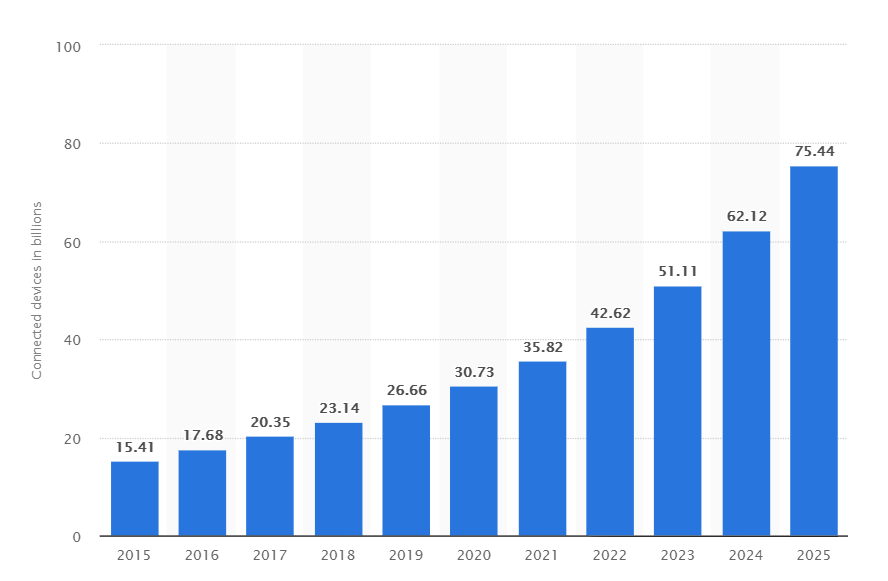
It is therefore logical to expect a massive evolution of cyber-attacks against this type of equipment based on the observations of recent years. The more objects connected to the internet, the more attack there will be.
In order to study the behavior of attackers, to discover security flaws and new types of malware, it is necessary to set up malicious behavior analysis systems.
What is a Honeypot ?
As I said before, it is necessary to set up systems to study the behavior of the attackers.This is where a system called Honeypot comes in.
What is it ?
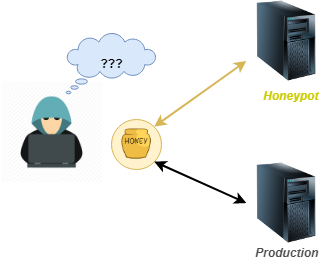
A Honeypot is a computer system for the purpose of "luring" attackers by simulating the behavior of a real system. The goal is to expose machines on the internet (often, they are virtual machines in a specially dedicated network that are used), and to "monitor" them to retrieve information about the attackers: their action, the vulnerabilities of security of exposed systems, etc.
Of course, the system should not arouse the suspicion of the attacker: They must not realize that it is a honeypot.
All communications established with a honeypot are considered suspicious: legitimate users have no reason to access them.
There are two types of Honeypot :
Honeypot with low interaction
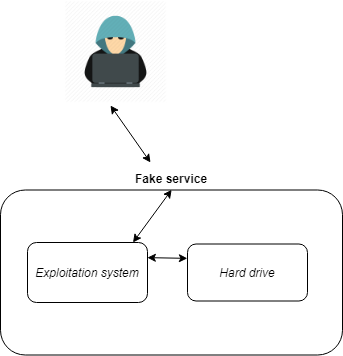
Honeypots with low interaction have a low level of interaction and often consist of
emulate operating systems and services. Activity is therefore limited to the degree
of emulation offered by the honeypot.
Thus, these honeypots offer few privileges to
the intruder who will have a limited scope.
Thus a low interaction honeypot only offers false services that do not return
never no answer. For example, the Honeypot can emulate an FTP service on port 21,
but emulate only the login command, or emulate other commands. The pirate tries to
to connect to these services and to execute orders there (such services may
resemble a listening socket that only logs the different packets it receives).
The fact that the hacker does not receive an answer is not a problem in some cases because he can
always see the result of his order.
With this type of honeypot the hacker never really interacts with the system hosting the
false services. The security of the system is maintained provided that the security rules
are also applied to false services.
An evolution of low interaction Honeypots, allows emulated services to send back
mostly fake answers to pirates so as to give him some leads or to confuse him
without necessarily intriguing him.
This implementation requires a very good knowledge of the protocols relating to fake
services. It is therefore quite difficult to put in place.
Honeypot with strong interaction
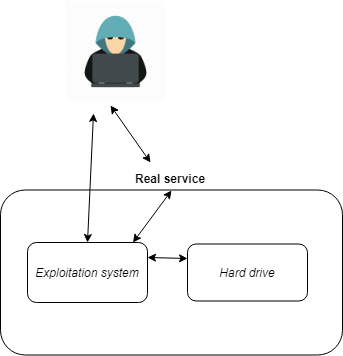
Honeypots with strong interaction are different because they often involve the use of
real operating systems and real applications. This is not about emulation, we
provides the attacker with something real. The risks are many since our
machine is intended to be compromised.
One of the advantages of this solution is that it is possible to obtain a lot of information,
because as attackers have access to real systems, one can examine all of their
behavior, and thus analyze their methods and the tools they use, whether they are
new or not.
The second advantage is that this type of Honeypot does not make any assumptions about the
likely behavior of an attacker and captures everything he can. This type of environment
so lets discover new methods of attack that were not yet
suspected.
Nevertheless there is an increased risk that the attacker can use the real systems of the
Honeypot to attack other systems that are not Honeypots.
These Honeypots can do anything Honeypots with low interaction can do.
Moreover. On the other hand, they are more complicated to put in place and manage.
Production environment
The main objective of a production honeypot is to verify that the security measures are applied.
It also protects the real production systems: in fact, if you expose a machine with known vulnerabilities, the attacker will go more easily to it than to a production system. This allows somehow to "lure"
Generally, production-oriented honeyports are used by organizations that want to improve the protection of their network, discover vulnerabilities in their applications, and enhance their ability to detect attacks.
Research environment

Research Honeypots are a bit more complex to set up as they aim to collect as much information about attackers and their procedures as possible.
The main goal is to discover new vulnerabilities in exposed systems and services, and new malware.
What information will be collected?
The goal is to recover as much information as possible about an attack, which will be stored in a database:
- Listening to network traffic
- Recovery of sent files/malwares
- Dumps: memory, hard drive, active processes at the time of the attack
- ...
- What are the most attacked ports ?
- What are the actions most often performed by the attackers ?
- Which services are the most sought after (telnet, ftp, ...)?
- Of which countries come the biggest attacks ?
- What combinations of login / password are the most used ?
- and more others...
Conclusion and Infographic
The things you need to remember !
There are two types of honeypot:
- Honeypots with low interaction (fake emulated system)
- Honeypots with strong interaction (real system)
- In research environment (studies of attacks, statistics, prevention ...)
- In production environment (test security measures, divert attackers ...)
Follow me on Twitter to be informed of my new articles/infographics →
 (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with