Index
- About Nmap
- Host discovery
- Output
- Different types of scan
- Port Specifications
- Service and version detection
- Other options
- Synthetic table
- Download Synthetic table
- End of this article
About Nmap
Nmap is a free port scanner created by Fyodor and distributed by Insecure.org.
To scan ports on a remote computer, Nmap uses a variety of scanning techniques that rely on protocols such as TCP, IP, UDP, or ICMP.
Similarly, it relies on the responses it gets to particular queries to get an imprint of the IP stack, often specific to the system that uses it.
It is through this method that he can recognize the version of an operating system and the version of services (also called daemons) listening
Different types of scan
TCP SYN Scan (-sS)
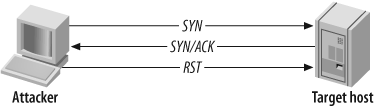
First, we have the default scan which is the SYN scan (-sS).
The advantage of this scan is that it does not terminate the connections, which makes it discreet.
He sends a SYN packet, and waits for an answer, as if he wanted to open a connection.
A SYN / ACK response will indicate that the port is listening (open), while an RST (reset) response will indicate that it is not listening.
If we do not have an answer or an error message, the port can be filtered.
 Source: oreilly.com
Source: oreilly.com
TCP Connect Scan (-sT)
Here, it is the same principle as the SYN scan, but Nmap establishes a connection with the remote machine to determine if the port is open, so it is a scan that is more noisy.
With this type of scan, files logs are quickly filled and old machines may not support as many connections.
I do not recommend using this type of scan unless we can not do SYN scan
UDP Scan (-sU)
UDP scanning is enabled with the -sU option. It can be combined with a TCP scan, like the SYN scan (-sS), to check both protocols during the same execution of Nmap.
Even though the most popular Internet services are based on TCP, UDP services are also widely used. DNS, SNMP or DHCP (ports 53, 161/162 and 67/68) are the three most common examples.
Do not neglect this type of scan.
For the next two scans, I used the definition given on the official website of nmap (https://nmap.org) because I can not explain them as well
TCP ACK Scan (-sA)
This scan is different than the others discussed so far in that it never determines open (or even open|filtered) ports.
It is used to map out firewall rulesets, determining whether they are stateful or not and which ports are filtered.
ACK scan is enabled by specifying the -sA option. Its probe packet has only the ACK flag set (unless you use --scanflags).
When scanning unfiltered systems, open and closed ports will both return a RST packet. Nmap then labels them as unfiltered, meaning that they are reachable by the ACK packet, but whether they are open or closed is undetermined. Ports that don't respond, or send certain ICMP error messages back, are labeled filtered.
TCP Idle Scan (-sI)
Fundamentally, an idle scan consists of three steps that are repeated for each port:
Synthetic table
This table was created by me. You can use it if you quote this article ;) ! (.xlsx file)
Download
| Options | Effects |
| Types of scan | |
| "-sS/sT/Sa/sW/sM" | Scans TCP SYN/Connect()/ACK/Windows/Maimon |
| "-sN/sF/sX" | Scans TCP Null, FIN, Xmas |
| "-sU" | Scan UDP |
| SCAN TCP | Test the connection to the ports (send SYN SYN/ACK ACK) |
| SCAN SYN | Just send a SYN and the connection is cut (more discreet) |
| Port Specifications | |
| "-p <range of ports>" | Scan the specified ports Example : -p 22; -p 1-1024; |
| "-p-" | Scan all the prots |
| "-Pn" | Disables host discoveries and forces Nmap to scan each system as if it were active : this is very useful for discovering hidden services |
| Service and version detection | |
| "-sV" | Test open ports to determine the listening service and its version |
| "-A " | Enables OS and version dectetion |
| "-sUV" | The goal is to trigger the sending of a response from the target. |
| Examples of commands | |
| nmap -p- -A -v -sS -U -Pn -sV <targ> | Long but complete scan |
| nmap -p- -v -A -sT -sU <targ> | Scan a little faster services tcp / udp |
| nmap -sU --top-port 20 <targ> | Scan the 20 most used ports in UDP |
| nmap -F <targ> | Scan the 100 most commonly used ports in TCP |
| Repporting | |
| "-oX myrepport.xml" | The report is generated in XML format |
| xsltproc myrepport.xml -o myreport.html | Convert the report to HTML to open in a browser |
End of this article
Through this article, I presented the different nmap options with tables. Of course, I did not present everything, only essential things.
If you want more details, nmap's documentation is very well done.
Follow me on Twitter to be informed of my new articles/infographics →  (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with
Buy me a coffee