Index
- What is Forensic Analysis ?
- How does a Forensic Analysis work ?
- Limit damage: Predicting an attack
- Tools for Forensic Analysis
What is Forensic Analysis ?

The purpose of this service is to trace the actions carried out by the hacker and the potential modifications that he would have made (filing of malicious files, alteration of existing files, etc.).
The ultimate goal is to determine the cause of the compromise, and gather evidence of fraud, which will identify the elements to be modified to correct the vulnerability.
How does a forensic analysis work ?
digital-forensic-analysis/
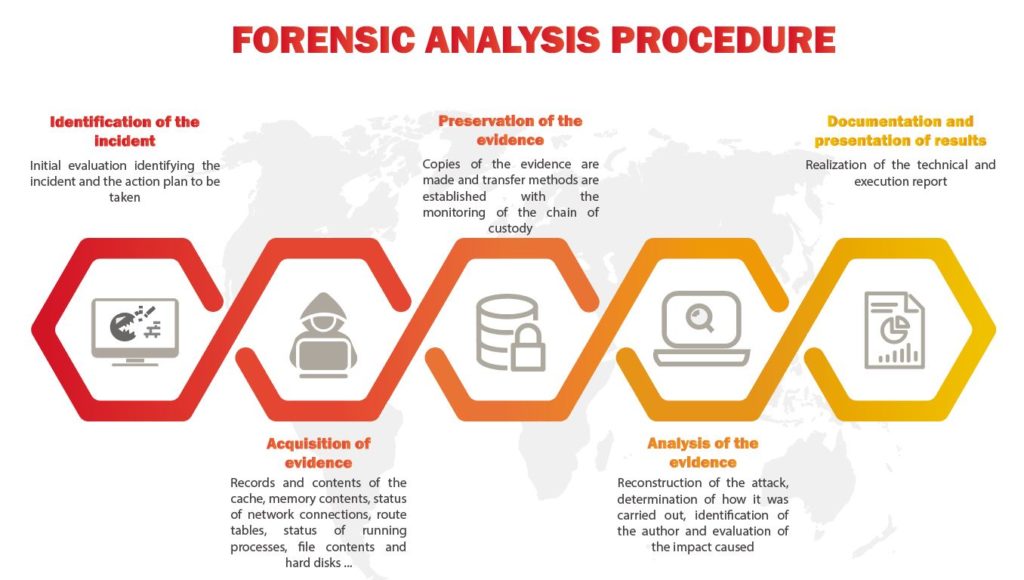
Identification of the incident
At first, it is necessary to determine the scope and the targeted technical environments, these can be very varied, it can be simply a computer, an application, but can go up to several servers, a complete network ... It all depends on the attack.
What is very important is not to rush. If you make decisions too quickly, you risk erasing important elements. For example: if one of your web server is infected, in an emergency you would be tempted to go back to a healthy backup. However, be sure to back up the current state of the server, to allow the analyst to collect information about the infected machine and identify the origin of the attack.
Acquisition of evidence
As we said in the previous step, it is important to save a copy of the current state of the machine when it is infected.
It is always recommended to start capturing the most to the least data. The order of volatility is:
Another essential knowledge for the forensic analyst is the knowledge of log files. The log files are present to allow you to accurately trace the behavior of a program or an attack.
Analysis of the evidence

Working on a frozen state of a disk brings several benefits to the analyst. This saves him from having to process "real-time" information, such as logs, and on the other hand, it does not interrupt the service. Finally, in case of error, the consequences will be limited. Once our image is up, we can start working. Often, it will be necessary to find files lost or erased (generally, an attacker erases the files of logs before leaving the machine).
You should know that when you erase a file from your hard drive, you do not really erase it, you only erase its reference. Indeed, the file system can be seen as a tree containing, for each file, its address on the disk, its size, its permissions, its name and a set of information necessary for the system. This information is stored in the tree in a data structure called "inode".
When you delete a file from your disk, it is only this inode that is deleted, and the space occupied by the file on the disk is then referenced in the tree as "available space"; this space will be rewritten later at the option of file creations.
This is why you freeze the state of the disc as quickly as possible to avoid rewriting and maximize your chances of recovery.
Documentation and presentation of results
This phase consists in drawing conclusions from the results obtained as a result of our analysis, and if the evidence permits, identify a suspect potential at the origin of the attack.
Once the exam is completed, the results are reported, along with a detailed description of the steps taken during the survey.
A review report usually includes the following details: information about the acquisition phase (who did the review, when it was done, what software / hardware tools were used, and what version numbers ), detailed information about the examination phase, such as descriptions of the medium being examined (volatile memory, hard disk, etc.).
This allows another reviewer to identify what has been done and access the results independently.
As a result of this conclusion, protective measures will be required to ensure that this incident does not reoccur.
Limit damage: Predicting an attack

React in case of compromise
MOST IMPORTANT
Do not restore to an earlier point without saving the state during compromise.
Tools for Forensic Analysis
Follow me on Twitter to be informed of my new articles/infographics →
 (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with